Privacy
By MacRumors Staff
Privacy How Tos

iOS 15: How to Hide Your IP Address From Trackers in Safari
In iOS 15, Apple updated its Intelligent Tracking Prevention feature in Safari to prevent trackers from accessing your IP address in order to build a profile about you. Intelligent Tracking Prevention, which Apple began implementing in 2017, is a privacy-focused feature meant to make it harder for sites to track users across the web, preventing browsing profiles and histories from being...
Read Full Article
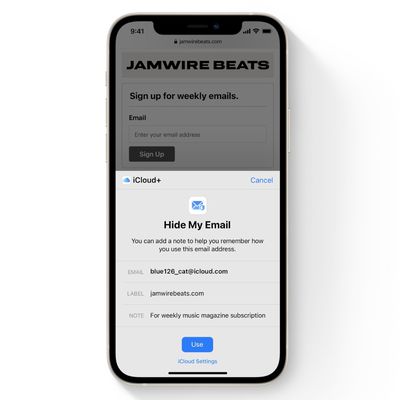
iOS 15: How to Create a 'Hide My Email' Private Address
With iOS 15 and Hide My Email, you can create unique, random email addresses that forward to your personal inbox whenever you want to keep your personal email address private. This is especially useful if you think that a business or website is likely to share your email address with ad agencies or other third-parties for marketing purposes. Providing them with a dummy address means you can ...

iOS 15: How to Change Where 'Hide My Email' Addresses Forward
With iOS 15 and the Hide My Email feature exclusive to iCloud+ subscribers, you can create unique, random email addresses that forward to your personal inbox whenever you want to keep your personal email address private. Hide My Email addresses are really useful if you think that a business or website is likely to share your email address with ad agencies or other third-parties for...

iOS 15: How to Deactivate or Delete a 'Hide My Email' Private Address
In iOS 15, paid iCloud+ plans feature Hide My Email, which lets you create unique, random email addresses that forward messages to your personal inbox whenever you want to keep your personal email address private. They're really useful if you think that a business or website is likely to share your email address with ad agencies or other third-parties for marketing purposes. Providing them...

iOS 15: How to Use Hide My Email
With the introduction of iOS 15, Apple rebadged its paid iCloud plans to "iCloud+" to reflect the fact that subscribers now get access to additional privacy features like Private Relay and Hide My Email. This article explains what Hide My Email is and how to use it. Hide My Email builds on the idea of Sign in With Apple by providing you with unique, random email addresses that forward to...

How to Adjust iCloud Private Relay IP Address Settings
As part of iOS 15, Apple introduced iCloud Private Relay, a feature of all iCloud+ paid plans that's designed to encrypt all of the traffic leaving your device so no one can intercept it or read it. Private Relay works by sending web traffic to a server that is maintained by Apple to strip the IP address. Once the IP info has been removed, Apple sends the traffic to a second server...

iOS 15: How to Turn iCloud Private Relay On and Off
Alongside iOS 15, Apple introduced an iCloud+ service that adds new features to its paid iCloud plans (upgraded iCloud storage tiers start at $0.99). One of these features is iCloud Private Relay, which is designed to encrypt all of the traffic leaving your device so no one can intercept it or read it. Private Relay sends web traffic to a server that is maintained by Apple...
Privacy Articles

Apple Wins Early Victory Against Spyware Maker NSO Group in Court
Apple has dealt a blow against spyware maker NSO Group and the Israeli firm's efforts to move Apple's lawsuit against it to its home country. Apple in November 2021 sued the group and its parent company with the aim of holding it accountable for targeting Apple users with spyware used for surveillance purposes. Judge Donato denied NSO's motion to dismiss Apple's case "in all respects," and...
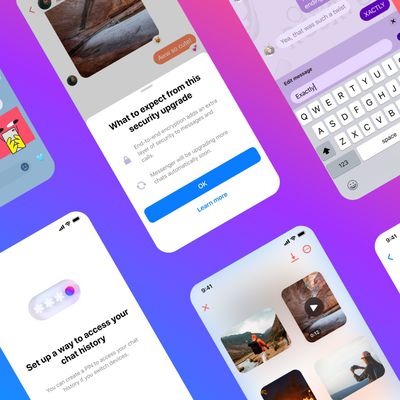
Facebook Messenger Rolls Out End-to-End Encryption by Default
Meta is rolling out end-to-end encryption for personal messages and calls on Messenger and Facebook, finally delivering on a pledge it committed to some time ago. Messenger encryption originally arrived in 2016 in the form of "secret conversations," and plans to extend the platform's cryptographic features have been floated ever since. According to Loredana Crisan, Head of Messenger,...
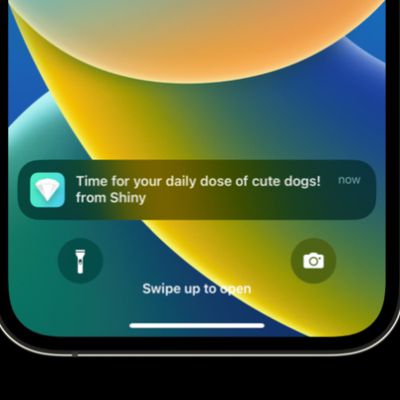
Apple Confirms Governments Using Push Notifications to Surveil Users
Unidentified governments are surveilling smartphone users by tracking push notifications that move through Google's and Apple's servers, a US senator warned on Wednesday (via Reuters). In a letter to the Department of Justice, Senator Ron Wyden said foreign officials were demanding the data from the tech giants to track smartphones. The traffic flowing from apps that send push notifications...

WhatsApp Now Lets You Hide Your IP Address During Calls
WhatsApp has introduced a new privacy feature that lets you hide your IP address from whoever you call over the encrypted communications platform. As it stands, one-to-one calls over WhatsApp are established as a direct peer-to-peer connection between users. While this ensures the best possible voice quality, it means the connected devices must reveal their IP addresses to each other....

Apple Accused of 'Hypocrisy' by Ad Industry Coalition Over Its Anti-Tracking Policy
Apple has been accused of "hypocrisy" and "cynicism" over its iPhone anti-tracking policy by an ad industry trade group that includes Meta and Google as members. The Interactive Advertising Bureau (IAB) is an organization that develops standards to be used across the industry to control and regulate online advertising. It has Google, Meta, Adobe, and many other companies as members. This...
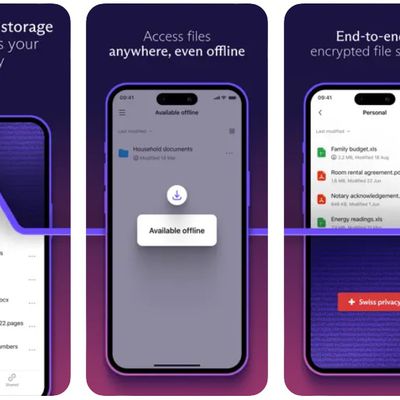
Proton Drive iOS and Android Apps Now Available for Encrypted Cloud Storage
Swiss-based privacy startup Proton today announced the availability of mobile apps for its Proton Drive cloud storage service, providing users with an easier way to securely upload, store, and share files from their iOS and Android devices. All files and folders uploaded to the storage service are protected by Proton's open-source, publicly-audited end-to-end encryption, which uses on-device ...

ProtonMail Unifies Encrypted Mail, Calendar, VPN, and Storage Services Under New 'Proton' Brand
Swiss-based encrypted email provider ProtonMail today announced a restructuring of its privacy-first services, bringing them under a new unifying brand name: Proton. Today, we are undertaking our biggest step forward in the movement for an internet that respects your privacy. The new, updated Proton offers one account, many services, and one privacy-by-default ecosystem. You can now enjoy...
Brave Browser for iOS Gains New 'Privacy Hub' and Enhanced Fingerprinting Protections
Privacy-focused browser Brave has updated its iOS app with a new Privacy Hub feature that displays a summary of the trackers it has blocked for specific sites or over a given time span. Similar to Safari’s Privacy Report, the new Privacy Hub in version 1.38 of the browser is designed to educate users about trackers and other privacy threats Brave is blocking. This update also improves...

Apple Scrapped Plans to Let Users Use Siri to Make Purchases Due to Privacy Concerns
Three years ago, Apple explored letting users use Siri to make purchases for apps and services, similar to how users can use Amazon's Alexa to place orders online, but engineers scrapped the idea following privacy concerns, according to a new report today by The Information. The report highlights how engineers at Apple have limited access to how users use Apple's services, such as Apple TV+ ...

watchOS 8.5 Fixes Mail Privacy Protection Loophole That Could Expose IP Addresses
watchOS 8.5 fixes a security vulnerability in the Mail app that could leak a user's IP address when downloading remote content, security researchers have found. Last year, it emerged that Apple's Mail Privacy Protection feature was undermined by a lack of Apple Watch support. Mail Privacy Protection was a new feature introduced with iOS 15, iPadOS 15, and macOS Monterey that hides your IP...

More Users Trust Amazon and Google to Handle Their Personal User Data Than Apple, Survey Suggests
According to a new survey, more users trust Amazon and Google to handle their personal user data and internet browsing activity than Apple, while users overwhelmingly distrust Facebook, TikTok, and Instagram. The survey conducted by The Washington Post sampled over 1,000 internet users in the U.S. about how much they trust Facebook, TikTok, Instagram, WhatsApp, YouTube, Google, Microsoft,...
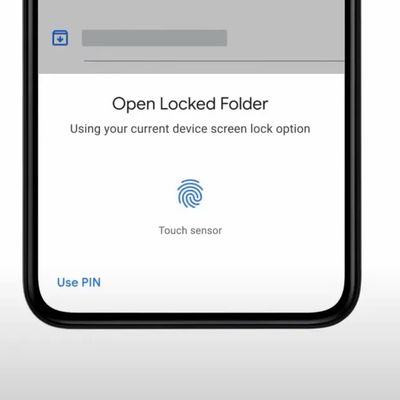
Google Photos 'Locked Folder' Feature for Pixel Phones Coming to iOS
Google Photos users on iPhone and iPad will soon be able to lock their most sensitive images in a special passcode-protected folder, thanks to a new feature coming to the iOS app (via The Verge). Currently exclusive to Pixel phones, the privacy-oriented Locked Folder feature allows users to save photos and videos in the app within a separate space that requires a passcode or fingerprint to...

Firefox 91 Update Strengthens Online Privacy With Enhanced Cookie Protection
Mozilla has announced the public release of Firefox 91, featuring an enhanced version of its Total Cookie Protection for individual websites. When you browse the web on your devices, websites will often leave cookies on your system so that they can remember you and what your preferences are. Some cookies are genuinely useful, as they allow sites to save your personal information (such as...













