Researchers from F-Secure, Webroot, and Avast have uncovered Janicab.A, a new trojan that was discovered as a threat to Macs last week and Windows users on Monday, with findings being published recently.
For OS X users, Janicab.A was signed with a valid Apple Developer ID and also uses a special unicode character known as a "right-to-left override" (RLO) that is used in email malware attacks. From there, the trojan uses a YouTube page to hijack infected computers, directs them to command-and-control (C&C) servers, and then leaves the server and hides the infection by making the malware appear as a harmless PDF or DOC file.
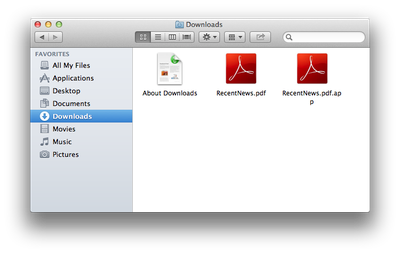
Webroot writes:
After a relatively long lag period without seeing any particular new and exciting Mac malware, last week we saw the surfacing of a new and interesting method of compromising the OSX system. Malware authors have taken a new approach by altering file extensions of malicious .app packages in order to trick users into thinking they are opening relatively harmless .pdf or .doc files. Changing file extensions in Mac OSX can be tricky due to a built in security feature of the OS that detects attempts to change the extension and automatically annexes the extension of its correct file or package type.
This news comes after Apple updated security definitions to combat 'Yontoo', an adware trojan this past March, while also regularly dealing with Java-related vulnerabilities. Apple introduced Gatekeeper in OS X Mountain Lion in order to better deal with security threats, offering a way for users to restrict installation of apps to those signed by Apple-issued Developer IDs.




















Top Rated Comments
(I'm guessing the File Quarantine feature should have this added as well by now)
It gets an article on MacRumors
:D
Should've used Preview.app PDF icon instead.
New because of the .app part maybe, but .pdf.exe is not a new approach by any means.
Also, who here uses Adobe for PDFs? (beyond filling out that one form that didn't work right in Preview for some reason)