Earlier this month, privacy issues related to the uploading of users' address books to developers' servers were cast into the limelight as Congress requested details from Apple on how private information is handled and protected. While Apple quickly responded to note that it would be addressing the issue by requiring explicit permission to be granted by users for apps to access their address book data, it has been a relatively open secret for some time that developers can gain access to a broad array of what might be considered private information, including photos, calendars, and other content.
The New York Times today is taking a closer look at the topic of photos and videos, noting how easy it is for developers to quietly gain access to such content when given permission to collect location information.
After a user allows an application on an iPhone, iPad or iPod Touch to have access to location information, the app can copy the user’s entire photo library, without any further notification or warning, according to app developers.
It is unclear whether any apps in Apple’s App Store are actually doing this. Apple says it screens all apps submitted to the store, and presumably it would not authorize an app that clearly copied a person’s photos without good reason. But copying address book data was also against Apple’s rules, and the company let through a number of popular apps that did so.
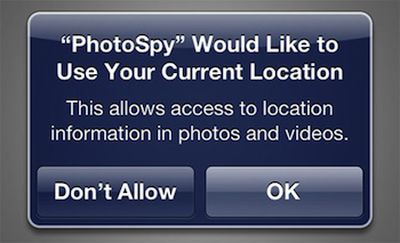
The New York Times tested this behavior by commissioning an iOS developer to write a simple test application dubbed "PhotoSpy" that demonstrates how a simple pop-up requesting permission to access location information can actually lead to broad access to all photos and videos in a user's photo library on the device.
When the “PhotoSpy” app was started up, it asked for access to location data. Once this was granted, it began siphoning photos and their location data to a remote server. (The app was not submitted to the App Store.)
Apple and other mobile app distributors recently signed on to a new agreement with the California Attorney General's office that will see the companies making it easier for users to examine privacy policies associated with apps before they download them. And with pressure mounting on Apple to take further steps to ensure that apps can access only information explicitly permitted by users, many are undoubtedly hoping that more changes are coming in the relatively near future.
Update: The Verge reports that "sources familiar with the situation" have indicated the photo and video access is a bug and that a fix is in the works.
We spoke to sources familiar with the situation, and were informed that a fix is most likely coming for the loophole. According to the people we talked to, Apple has been made aware of the issue and is likely planning a fix with an upcoming release of iOS. Those sources also confirmed that the ability to send your photos and videos to a third-party is an error, not an intended feature. If we had to guess, the fix will likely come alongside a patch for Apple's other recent security issue — the ability for apps to upload your address book information without warning.



















Top Rated Comments
1. You asked the user for permission (although not explicitly for what you did).
2. You did not submit this to the App Store (aka, have no idea whether it would have been approved)
Gotcha. Thanks, but you couldn't have put together a more irrelevant example of an App Store App that takes data without permission.
Nope. Android permission can be easily bypassed by Android malware:
http://www.theregister.co.uk/2011/11/30/google_android_security_bug/
There is absolutely no way you can defend against that unless you have a curated approach. If it's a file manager, it needs access to your files. Likewise in the NY Times example, if it is a photo editing app, it needs access to your photos. There is no way getting around it. Someone has to actually test the app to know what exactly it will do once it has access to some particular part of your device. That's why Android is a goldmine for malware and privacy invaders.
Having access to private data is not the same thing as malware??? :confused:
- contacts
- calendars
- photos
- videos
Nothing new. Although, highly severe and critical.
Apple made a mess out of them. They should have treated this data, the way they treat locations in general. Too lenient.
Well, it does, and that's because photos might contain location information in the metadata.
So, iPhone users can at least be assured that their photos aren't being accessed if the app doesn't ask permission for location data.
This problem has existed since Day 1, and has been ignored by both Apple and millions of users. It goes to show you how easily we trust those who should not be trusted today. I am baffled at the phenomena.
That the public doesn't care is illustrated by the widespread use of Facebook.
It's going to bite many people. I do think that the public will take an about face over the next couple of years, as the chickens come home to roost. I think the major factor driving this will be the largescale abandonment of the traditional resume by job-seekers and employers.
Lots of people are going to find that they screwed themselves royally.