Alleged iOS Security Flaw Enables Malicious Apps to Secretly Log User Touch Inputs
Researchers from security firm FireEye have revealed a new bug in iOS that enables a malicious app to monitor and log a user's touch inputs and button uses while running in the background, reports Ars Technica. The exploit reportedly targets a flaw in iOS' multitasking capabilities to capture user inputs, and allows for them to be sent to a remote server.
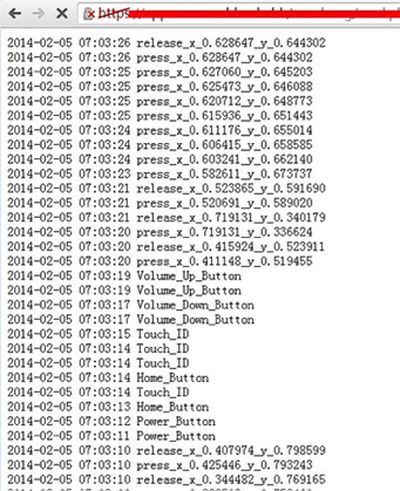
To demonstrate the flaw, the researchers created a proof-of-concept monitoring app and developed approaches to "bypass" Apple's App Store Review process effectively. Once the app was installed on an iOS device, actions including keyboard inputs, use of the volume, home, and power buttons, screen touches with exact coordinates, and Touch ID events were all captured. The researchers also noted that disabling iOS 7's "Background App Refresh" setting would not disable a malicious app from logging data, as the only present solution to the problem is to manually remove apps from the task switcher.
FireEye also spoke about the flaw being identified in current versions of iOS:
Note that the demo exploits the latest 7.0.4 version of iOS system on a non-jailbroken iPhone 5s device successfully. We have verified that the same vulnerability also exists in iOS versions 7.0.5, 7.0.6 and 6.1.x. Based on the findings, potential attackers can either use phishing to mislead the victim to install a malicious/vulnerable app or exploit another remote vulnerability of some app, and then conduct background monitoring.
The group added that it is actively working with Apple on the issue, although the company has yet to comment publicly. The news comes less than a week after Apple issued iOS 7.0.6 in response to a SSL vulnerability that allowed a hacker to capture or modify data from Safari in supposedly secure sessions.
The SSL security bug was also found to be present in OS X, as new research over the weekend revealed that additional apps such as FaceTime and iMessage could be compromised. Apple confirmed to Reuters that it will issue an OS X software update "very soon" to patch the bug.
Popular Stories
Apple today released several open source large language models (LLMs) that are designed to run on-device rather than through cloud servers. Called OpenELM (Open-source Efficient Language Models), the LLMs are available on the Hugging Face Hub, a community for sharing AI code. As outlined in a white paper [PDF], there are eight total OpenELM models, four of which were pre-trained using the...
Apple is set to unveil iOS 18 during its WWDC keynote on June 10, so the software update is a little over six weeks away from being announced. Below, we recap rumored features and changes planned for the iPhone with iOS 18. iOS 18 will reportedly be the "biggest" update in the iPhone's history, with new ChatGPT-inspired generative AI features, a more customizable Home Screen, and much more....
Apple has announced it will be holding a special event on Tuesday, May 7 at 7 a.m. Pacific Time (10 a.m. Eastern Time), with a live stream to be available on Apple.com and on YouTube as usual. The event invitation has a tagline of "Let Loose" and shows an artistic render of an Apple Pencil, suggesting that iPads will be a focus of the event. Subscribe to the MacRumors YouTube channel for more ...
Apple has dropped the number of Vision Pro units that it plans to ship in 2024, going from an expected 700 to 800k units to just 400k to 450k units, according to Apple analyst Ming-Chi Kuo. Orders have been scaled back before the Vision Pro has launched in markets outside of the United States, which Kuo says is a sign that demand in the U.S. has "fallen sharply beyond expectations." As a...
Apple is finally planning a Calculator app for the iPad, over 14 years after launching the device, according to a source familiar with the matter. iPadOS 18 will include a built-in Calculator app for all iPad models that are compatible with the software update, which is expected to be unveiled during the opening keynote of Apple's annual developers conference WWDC on June 10. AppleInsider...
Best Buy is discounting a collection of M3 MacBook Pro computers today, this time focusing on the 14-inch version of the laptop. Every deal in this sale requires you to have a My Best Buy Plus or Total membership, although non-members can still get solid second-best prices on these MacBook Pro models. Note: MacRumors is an affiliate partner with Best Buy. When you click a link and make a...





















Top Rated Comments
If you know the exact coordinates you can simply overlay the iOS Keyboard and extract everything the user typed in, including passwords, logins or other personal information. :rolleyes: But yeah, no security issue here. LOL.
those people closing all their apps don't look so silly after all :p:D:p
The fact that x and y co-ordinates of each touch or release event is captured, could be used as a key-logger once the boundries of each key on the soft keyboard have been worked out.
Business as usual then......