Newly Discovered Mac Malware Captures and Stores Screenshots
New Mac spyware was discovered earlier this week on a computer at the Oslo Freedom Forum, an annual human rights conference. Located by computer security researcher Jacob Appelbaum, the malware, which has been deemed OSX/KitM.A, is currently being investigated by anti-virus company F-Secure, reports CNET.
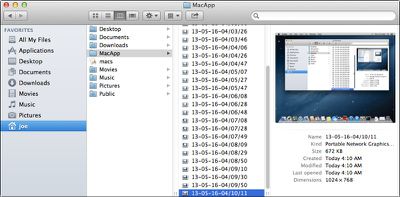
The malware is a backdoor application called "macs.app," which launches automatically upon login and captures screenshots that it then sends to a MacApp folder in the user's home directory. Two command-and-control servers, located at securitytable.org and docsforum.info, are associated with the malware, but one does not function and the other gives a "public access forbidden" message.
Interestingly, the malware is signed with an Apple Developer ID, which is designed to prevent the installation of malware. Apps that are unsigned are blocked by default by Apple's Gatekeeper security option.
This bit of malware is somewhat unique in that it is signed with what appears to be a valid Apple Developer ID associated with the name Rajender Kumar. Though not an uncommon name, this may be a reference to the late Bollywood actor of a similar name. Regardless, the use of the ID appears to be an attempt to bypass Apple's Gatekeeper execution prevention technology.
Currently, F-Secure is investigating where the malware originated, and though it does not appear to be widespread, it can be mitigated by removing the macs.app program from the log-in menu. Apple often addresses malware threats quickly, and has the ability to revoke the developer ID to further limit the spread of the software.
Popular Stories
Apple today released several open source large language models (LLMs) that are designed to run on-device rather than through cloud servers. Called OpenELM (Open-source Efficient Language Models), the LLMs are available on the Hugging Face Hub, a community for sharing AI code. As outlined in a white paper [PDF], there are eight total OpenELM models, four of which were pre-trained using the...
Apple is set to unveil iOS 18 during its WWDC keynote on June 10, so the software update is a little over six weeks away from being announced. Below, we recap rumored features and changes planned for the iPhone with iOS 18. iOS 18 will reportedly be the "biggest" update in the iPhone's history, with new ChatGPT-inspired generative AI features, a more customizable Home Screen, and much more....
Apple has announced it will be holding a special event on Tuesday, May 7 at 7 a.m. Pacific Time (10 a.m. Eastern Time), with a live stream to be available on Apple.com and on YouTube as usual. The event invitation has a tagline of "Let Loose" and shows an artistic render of an Apple Pencil, suggesting that iPads will be a focus of the event. Subscribe to the MacRumors YouTube channel for more ...
Apple has dropped the number of Vision Pro units that it plans to ship in 2024, going from an expected 700 to 800k units to just 400k to 450k units, according to Apple analyst Ming-Chi Kuo. Orders have been scaled back before the Vision Pro has launched in markets outside of the United States, which Kuo says is a sign that demand in the U.S. has "fallen sharply beyond expectations." As a...
Apple is finally planning a Calculator app for the iPad, over 14 years after launching the device, according to a source familiar with the matter. iPadOS 18 will include a built-in Calculator app for all iPad models that are compatible with the software update, which is expected to be unveiled during the opening keynote of Apple's annual developers conference WWDC on June 10. AppleInsider...
Best Buy is discounting a collection of M3 MacBook Pro computers today, this time focusing on the 14-inch version of the laptop. Every deal in this sale requires you to have a My Best Buy Plus or Total membership, although non-members can still get solid second-best prices on these MacBook Pro models. Note: MacRumors is an affiliate partner with Best Buy. When you click a link and make a...





















Top Rated Comments
Only if Apple can't pull the plug. That is the purpose of the certificate--not prevention of attempts in the first place.
When did Apple receive the details on this? And what do they need to do to verify? (Obviously they can't simply obey any random request to shut a developer down, so there must be some verification steps.)