Transmission Malware Transmitted Through Server Hack, Downloaded 6,500 Times
Over the weekend, the first instance of Mac ransomware was found in a malicious update to the Transmission BitTorrent client. Version 2.90 of Transmission downloaded from the Transmission website was infected with "KeRanger" ransomware.
"Ransomware" is a class of malware that encrypts a user's hard drive and files, demanding money to decrypt it. In this case, KeRanger would have required Mac users to shell out a bitcoin for decryption, equivalent to approximately $400.
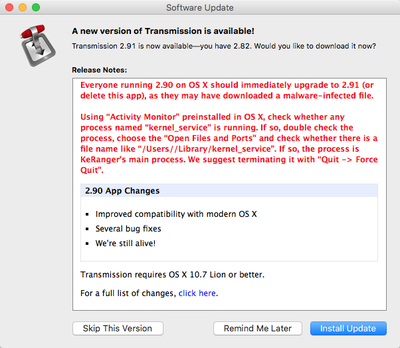
The developers behind Transmission have shared some additional details on the attack with Reuters, giving us some insight into how it occurred. The server that delivers the Transmission software to customers was breached in a cyber attack, allowing the KeRanger malware to be added to the disk-image of its software.
Transmission representative John Clay told Reuters via email that the ransomware was added to disk-image of its software after the project's server was compromised in a cyber attack.
"We're not commenting on the avenue of attack, other than to say that it was our main server that was compromised," he said. "The normal disk image (was) replaced by the compromised one."
During the time that the malware-infected version of Transmission was available, it was downloaded approximately 6,500 times before the vulnerability was discovered. Security on the server has since been increased, ensuring a similar attack can't occur a second time.
On Sunday, Transmission's developers released software updates to block the malicious software and to remove it from the Macs of users who had unwittingly installed the malicious version. Apple also updated its software protections to keep the malware from affecting Mac users and to prevent the bad version from being installed on additional machines.
Customers who have downloaded the Transmission BitTorrent client should make sure they have updated the software to version 2.92, which will remove the malware from infected computers. Additional details on how to determine if you have the malware installed are available through Palo Alto Networks.
Popular Stories
Apple is not expected to release a standard iPhone 18 model this year, according to a growing number of reports that suggest the company is planning a significant change to its long-standing annual iPhone launch cycle.
Despite the immense success of the iPhone 17 in 2025, the iPhone 18 is not expected to arrive until the spring of 2027, leaving the iPhone 17 in the lineup as the latest...
Apple's restrained artificial intelligence strategy may pay off in 2026 amid the arrival of a revamped Siri and concerns around the AI market "bubble" bursting, The Information argues.
The speculative report notes that Apple has taken a restrained approach with AI innovations compared with peers such as OpenAI, Google, and Meta, which are investing hundreds of billions of dollars in data...
The Apple Fitness+ Instagram account today teased that the service has "big plans" for 2026. In a video, several Apple Fitness+ trainers are shown holding up newspapers with headlines related to Apple Fitness+.
What's Apple Fitness+ Planning for the New Year?
Something Big is Coming to Apple Fitness+
The Countdown Begins. Apple Fitness+ 2026 is Almost Here
2026 Plans Still Under ...
iPhone 17 Pro and Pro Max owners are having trouble with the speakers of their devices, and have complained about a static or hissing noise that occurs when the iPhone is charging.
There are multiple discussions about the issue on Reddit, the MacRumors forums, and Apple's Support Community, where affected users say there is a noticeable static noise "like an old radio." Some people report...
Apple is rumored to be introducing a foldable iPhone in September 2026, and since it will bring the biggest form factor change since the iPhone was introduced in 2007, curiosity about the design is high. A 3D designer created an iPhone Fold design based on rumors, and we printed it out to see how it compares to Apple's current iPhones.
Subscribe to the MacRumors YouTube channel for more ...
Apple hasn't updated the Apple TV 4K since 2022, and 2025 was supposed to be the year that we got a refresh. There were rumors suggesting Apple would release the new Apple TV before the end of 2025, but it looks like that's not going to happen now.
Subscribe to the MacRumors YouTube channel for more videos.
Bloomberg's Mark Gurman said several times across 2024 and 2025 that Apple would...
Apple hasn't updated the Mac Pro since 2023, and according to recent rumors, there's no update coming in the near future. In fact, Apple might be finished with the Mac Pro.
Bloomberg recently said that the Mac Pro is "on the back burner" and has been "largely written off" by Apple. Apple apparently views the more compact Mac Studio as the ideal high-end pro-level desktop, and it has almost...
Apple today added the final 13-inch MacBook Air powered by Intel processors, the Apple Watch Series 5, and additional products to its vintage products list. The iPhone 11 Pro was also added to the list after the iPhone 11 Pro Max was added back in September.
The full list of products added to Apple's vintage and obsolete list today:
MacBook Air (Retina, 13-inch, 2020)
iPhone 8 Plus 128GB ...