Malware
By MacRumors Staff
Malware Articles
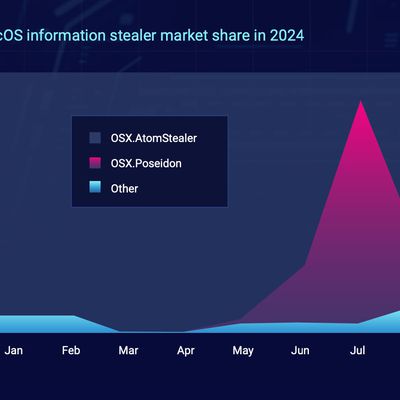
'Stealers' Are an Increasingly Common Mac Malware
macOS stealers are becoming an increasingly common type of malware on the Mac, according to the 2025 State of Malware report that Malwarebytes shared this week.
Most Mac malware has historically been VSearch adware or the Genieo browser hijacker, but more malicious malware is on the rise, and 2024 saw a new wave of information stealing malware hit the Mac.
Stealers are designed to locate...
Read Full Article 52 comments

Malware With Screen Reading Code Found in iOS Apps for the First Time
Malware that includes code for reading the contents of screenshots has been found in suspicious App Store apps for the first time, according to a report from Kaspersky.
Dubbed "SparkCat," the malware includes OCR capabilities for sussing out sensitive information that an iPhone user has taken a screenshot of. The apps that Kaspersky discovered are aimed at locating recovery phrases for...
'Cthulhu Stealer' macOS Malware Can Steal Keychain Passwords, Web Browsing Info, Crypto Wallets, and More
Apple's Macs are less targeted by malware than Windows PCs, but that doesn't mean they are immune. Increasingly, insidious types of Mac malware are being developed that have researchers concerned enough to issue public warnings, and that's the case again today.
As reported by Hacker News, Cado Security has identified a malware-as-a-service (MaaS) targeting macOS users named "Cthulhu...

Common Windows Malware Can Now Infect Macs
A common form of malware on Windows systems has been modified into a new strain called "XLoader" that can also target macOS (via Bleeping Computer).
Derived from the Formbook info-stealer for Windows, XLoader is a form of cross-platform malware advertised as a botnet with no dependencies. It is used to steal login credentials, capture screenshots, log keystrokes, and execute malicious files. ...
Apple's Notarization Process Repeatedly Approved Malware for Mac
Apple mistakenly approved and notarized a common kind of malware for macOS on at least two occasions, reports TechCrunch.
Apple requires developers to submit their apps for security checks to run on macOS in a process called "notarization." Notarization was required from the launch of macOS Catalina. If software has not been notarized, it will be blocked by default in macOS.
Peter...

Malware Injected Into Xcode Projects Could Infiltrate Mac App Store
Last week, we reported on a severe new kind of Mac malware that has been found to infect via Xcode, discovered by security researchers at Trend Micro.
In an exclusive interview with MacRumors, the security researchers behind the discovery, Oleksandr Shatkivskyi and Vlad Felenuik, have provided more information about their research.
The malware, which is part of the XCSSET family, is "an ...

New Mac Malware Found to Infect via Xcode
Security researchers at Trend Micro have discovered a new kind of Mac malware which can "command and control" a target system.
The researchers described the malware, which is part of the XCSSET family, as "an unusual infection related to Xcode developer projects." The malware is unusual because it is injected into Xcode projects, and when the project is built, the malicious code is run. A...
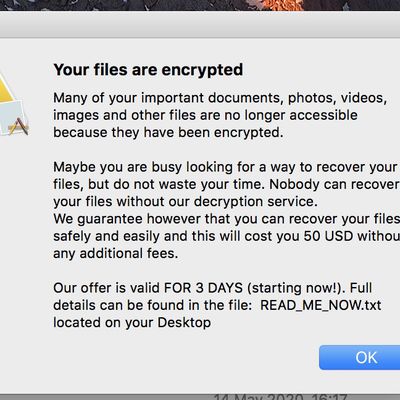
New Mac Ransomware Found in Pirated Mac Apps
There's a new 'EvilQuest' Mac ransomware variant that's spreading through pirated Mac apps, according to a new report shared today by Malwarebytes. The new ransomware was found in pirated download for the Little Snitch app found on a Russian forum.
Right from the point of download, it was clear that something was wrong with the illicit version of Little Snitch, as it had a generic installer...
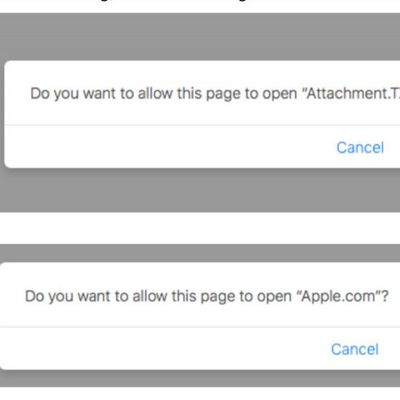
Security Researcher Shows How Remote macOS Exploit Hoodwinks Safari Users With Custom URL Schemes
A security researcher has demonstrated how macOS users are vulnerable to remote infection through a malicious exploit involving the "Do you want to allow..." popup that can be encountered when visiting websites in Safari.
In a lengthy breakdown, Patrick Wardle explains how the exploit utilizes document handlers, which request permission to open a link or a file in another app – like a PDF in ...
Malware Discovered That Can Control a Mac's Webcam and Keyboard, But It's Old and Possibly Abandoned
Earlier this year, researchers from security firm Malwarebytes discovered a piece of Mac malware called Fruitfly that reportedly spied on computers in medical research centers for years before being detected. Apple has since updated macOS to automatically detect the malware, safeguarding users.
However, a new variant of the Fruitfly malware has recently been discovered by Patrick Wardle, a...
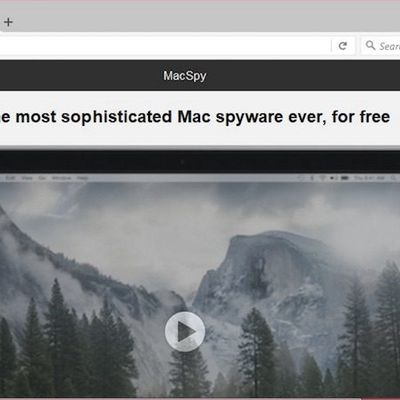
New Mac Malware Discovered on Dark Web as Security Experts Remind Mac Users Not to Be 'Overconfident'
Two new pieces of malicious software aimed at Mac computers have been discovered on the Dark Web, offered through Malware-as-a-Service (MaaS) and Ransomware-as-a-Service (RaaS) portals and estimated to have been up for around the past three weeks, beginning May 25. Originally spotted by Bleeping Computer, the two portals offer software called "MacSpy" and "MacRansom" as services for potential...

Source Code for Several Panic Apps Stolen via HandBrake Malware Attack
In early May, a mirror download server hosting popular Mac transcoder app HandBrake was hacked, and the legitimate version of HandBrake was replaced with a version infected with OSX.PROTON, a remote access trojan giving hackers root-access privileges to a Mac.
In a blog post shared today, Panic Inc. developer and co-founder Steven Frank said he downloaded the infected version of HandBrake,...

Handbrake Developers Issue Mac Security Warning After Mirror Download Server Hack
The developers of open source video transcoder app Handbrake have issued a security warning to Mac users after a mirror download server hosting the software was hacked.
The alert was issued on Saturday after it was discovered that the original HandBrake-1.0.7.dmg installer file on mirror server download.handbrake.fr had been replaced by a malicious file.
The affected server has been shut...
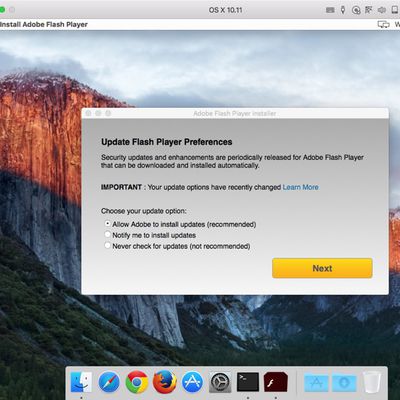
Windows 'Snake' Malware Ported to Mac, Imitates Adobe Flash Player Installer
Well-known Windows backdoor malware "Snake" has been ported to the Mac for the first time, according to MalwareBytes. Described as "highly-sophisticated," Snake (also called Turla and Uroburos) has been infecting Windows systems since 2008 and was ported to Linux systems in 2014 before making its way to the Mac.
The Snake malware was found earlier this week in an installer masquerading as...
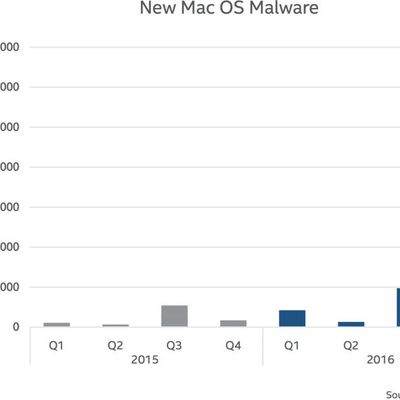
Malware Attacks on Macs Up 744% in 2016, Mostly Due to Adware
Malware attacks on Macs were up 744 percent in 2016, according to the latest Threat Report shared by McAfee Labs [PDF]. Mac users don't need to be overly alarmed, though, because much of that huge jump can be attributed to adware bundling. macOS malware samples jumped up 245 percent in the fourth quarter of 2016 alone just from adware.
Adware, while irritating, is less alarming than true...

BitTorrent Client Transmission Again Victimized by OS X Malware
Just five months after Transmission was infected with the first "ransomware" ever found on the Mac, the popular BitTorrent client is again at the center of newly uncovered OS X malware.
Researchers at security website We Live Security have discovered the malware, called OSX/Keydnap, was spread through a recompiled version of Transmission temporarily distributed through the client's official...
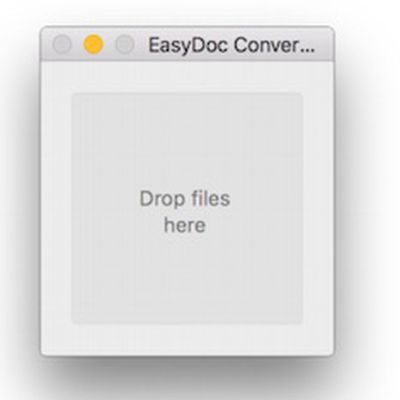
What You Need to Know About Mac Malware 'Backdoor.MAC.Eleanor'
Internet security software company Bitdefender's research lab has disclosed new malware targeting Macs called Backdoor.MAC.Eleanor [PDF]. Learn more about the malware and how to keep your Mac protected against attackers.
What is Backdoor.MAC.Eleanor?
Backdoor.MAC.Eleanor is new OS X/macOS malware arising from a malicious third-party app called EasyDoc Converter, which poses as a...
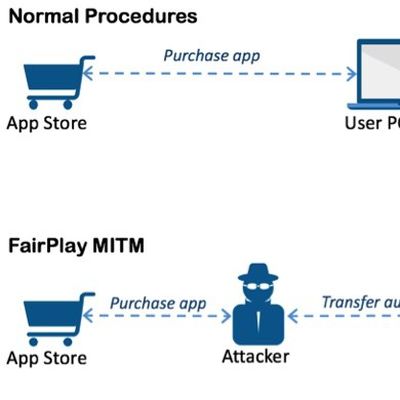
'AceDeceiver' iOS Trojan Spotted in China, Bypasses Apple's DRM Mechanism
A new iOS trojan has been found in the wild that's able to infect non-jailbroken iOS devices through PCs without the need to exploit an enterprise certificate. Named "AceDeceiver," the malware was discovered by Palo Alto Networks and is currently affecting iOS users in China.
AceDeceiver infects an iOS device by taking advantage of flaws in FairPlay, Apple's digital rights management (DRM)...
Apple Responds to YiSpecter Malware, Says Fix Was Implemented in iOS 8.4
Over the weekend, security site Palo Alto Networks detailed a new iOS malware that's able to infect non-jailbroken Apple devices using enterprise certificates and private APIs. It originated in Taiwan and China and was installed through several methods, including hijacking traffic from ISPs, an SNS worm on Windows, and offline app installation.
Called YiSpecter, the malware is able to...











