Security
By MacRumors Staff
Security How Tos
How to Check iCloud Keychain Password Security
Using iCloud Keychain, Apple's Safari browser stores and syncs all the passwords you use for different websites and apps through iCloud. And in iOS 14 and later, Apple provides security recommendations that warn you if a password you're using is putting your accounts at risk.
Safari securely monitors your saved passwords using strong cryptographic techniques, and regularly checks derivations ...
Read Full Article

How to Use Firefox Private Network to Encrypt Your Web Traffic
Mozilla this week began piloting its own browser-based VPN service, and if you're located in the U.S. you can start testing it for free right away.
Called the Firefox Private Network, the service promises Firefox users a more secure, encrypted path to the web that prevents eavesdroppers from spying on your browsing activity and hides your location from websites and ad trackers.
In that...

How to Encrypt a USB Flash Drive in macOS Mojave
In macOS Mojave, you can choose to encrypt and decrypt disks on the fly right from the desktop. Using this convenient Finder option, we're going to show you how to encrypt a USB flash drive (or "thumb drive"), which is useful if you're traveling light and want to take sensitive data with you for use on another Mac.
Finder uses XTS-AES encryption, the same encryption that FileVault 2 uses to...
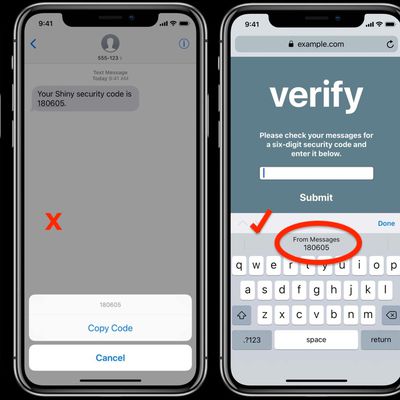
How to Use Secure Code AutoFill in iOS 12 and macOS Mojave
Most readers will have at some point received a two-factor authentication code delivered to them by SMS text message. Many apps and websites send the one-time codes to confirm that the person attempting to log in to an account is the legitimate account holder, and not just someone using a stolen password.
Depending on how notifications are set up on your iPhone, receiving a code via text...
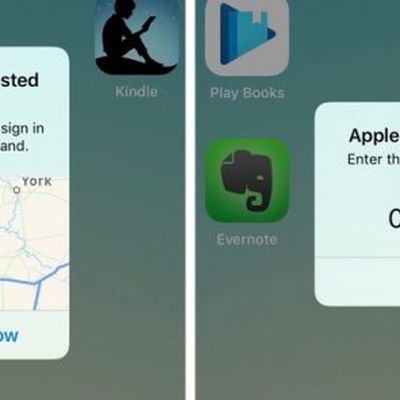
How to Secure Your Apple ID Using Two-Factor Authentication
Apple introduced two-factor authentication (2FA) in 2015 to provide an enhanced level of security when accessing Apple ID accounts. With 2FA enabled, you'll be the only person who can access your account, regardless of whether someone learns your password – as the result of a hack or a phishing scam, for example – so it's well worth taking the time to enable the feature. In this article,...
Security Articles

Cellebrite Unable to Unlock iPhones on iOS 17.4 or Later, Leak Reveals
Israel-based mobile forensics company Cellebrite is unable to unlock iPhones running iOS 17.4 or later, according to leaked documents verified by 404 Media. The documents provide a rare glimpse into the capabilities of the company's mobile forensics tools and highlight the ongoing security improvements in Apple's latest devices.
The leaked "Cellebrite iOS Support Matrix" obtained by 404 Media...

Proton Pass Multi-Platform Password Manager Launches on macOS
Swiss-based privacy startup Proton today announced the availability of Proton Pass for Mac and Linux, bringing the encrypted password manager to every platform for the first time.
Proton Pass features end-to-end encryption for all stored data, and includes a built-in two-factor authentication system, passkey support, and secure password sharing, as well as a Hide-My-Email feature to protect...
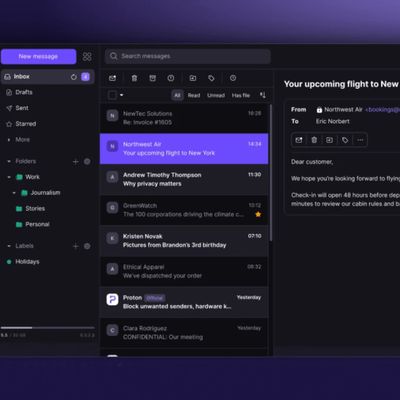
Proton Encrypted Mail Desktop App Now Available for Mac
Swiss-based privacy startup Proton today announced the availability of its end-to-end encrypted desktop mail app for macOS and Windows, with a Linux version in beta.
According to the company, the Proton Mail desktop app has been optimized to integrate with Macs, which means it can sync themes with the desktop's light or dark mode, display notifications natively, and offer instant switching...
PSA: Google Authenticator's Cloud-Synced 2FA Codes Aren't End-to-End Encrypted
Earlier this week, Google updated its Authenticator app to enable the backup and syncing of 2FA codes across devices using a Google Account. Now an examination by Mysk security researchers has found that the sensitive one-time passcodes being synced to the cloud aren't end-to-end encrypted, leaving them potentially exposed to bad actors.
Prior to the integration of Google Account support,...

LastPass Hacked for Second Time This Year
Password management app LastPass says it is investigating a security incident after an "unauthorized party" compromised its systems on Wednesday and gained access to some customer information.
The information was stored in a third-party cloud service shared by LastPass and parent company GoTo, said LastPass CEO Karim Toubba in a blog post. Toubba said the hackers used information stolen from ...
VPNs for iOS Are Broken and Apple Knows It, Says Security Researcher
Third-party VPNs made for iPhones and iPads routinely fail to route all network traffic through a secure tunnel after they have been turned on, something Apple has known about for years, a longtime security researcher has claimed (via ArsTechnica).
Writing on a continually updated blog post, Michael Horowitz says that after testing multiple types of virtual private network (VPN) software on...

Apple Outlines How It Will Notify Users Who Have Been Targeted by State-Sponsored Spyware Attacks
Earlier today, Apple announced that it had filed suit against NSO Group, the firm responsible for the Pegasus spyware that has been used in state-sponsored surveillance campaigns in a number of countries. NSO Group seeks to take advantage of vulnerabilities in iOS and other platforms to infiltrate the devices of targeted users such as journalists, activists, dissidents, academics, and government...

Apple's iOS 14.8 Update Fixes Zero-Click Exploit Used to Distribute Pegasus Spyware
Today's iOS 14.8 update addresses a critical vulnerability that Apple engineers have been working around the clock to fix, reports The New York Times.
Last week, The Citizen Lab informed Apple about a new zero-click iMessage exploit targeting Apple's image rendering library. Called FORCEDENTRY, the exploit could infect an iPhone, iPad, Apple Watch, or Mac with the Pegasus spyware, providing...
WhatsApp to Let Users Encrypt Chat Backups Uploaded to iCloud
WhatsApp has announced it will give its two billion users the option to upload their chat backups to Apple's iCloud using password-protected encryption.
Currently, WhatsApp on iPhone lets users back up their chat history to iCloud, but messages and media that users back up aren't protected by WhatsApp's end-to-end encryption while in Apple's cloud servers.
Given that Apple...

Apple Not Trying Hard Enough to Protect Users Against Surveillance, Researchers Say
Following the news of widespread commercial hacking spyware on targeted iPhones, a large number of security researchers are now saying that Apple could do more to protect its users (via Wired).
Earlier this week, it was reported that journalists, lawyers, and human rights activists around the world had been targeted by governments using phone malware made by the surveillance firm NSO Group...

Report: Pegasus Spyware Sold to Governments Uses Zero-Click iMessage Exploit to Infect iPhones Running iOS 14.6
Journalists, lawyers, and human rights activists around the world have been targeted by authoritarian governments using phone malware made by Israeli surveillance firm NSO Group, according to multiple media reports.
An investigation by 17 media organizations and Amnesty International's Security Lab uncovered a massive data leak, indicating widespread and continuing abuse of the commercial...
Find My Network Exploited to Send Messages
An exploit allows messages and additional data to be sent across Apple's Find My network, according to the findings of a security researcher.
Security researcher Fabian Bräunlein has found a way to leverage Apple's Find My network to function as a generic data transfer mechanism, allowing non-internet-connected devices to upload arbitrary data by using nearby Apple devices to upload the...

Apple Made Sudden Security Changes to its Chips in Fall 2020
Apple made unusual mid-production hardware changes to the A12, A13, and S5 processors in its devices in the fall of 2020 to update the Secure Storage Component, according to Apple Support documents.
According to an Apple Support page, spotted by Twitter user Andrew Pantyukhin, Apple changed the Secure Enclave in a number of products in the fall of 2020:Note: A12, A13, S4, and S5 products...

Facebook Data for Over 535 Million Users Leaked on Hacker Website
The personal details of more than 553 million Facebook users have been published on a website for hackers, according to multiple reports over the weekend.
The details appeared on Saturday, according to Business Insider, and are also available in 106 different country-based packages, included 32 million records on users in the US, 11 million on users in the UK, and 6 million on users in...

Apple Reportedly Patches XSS Vulnerability on iCloud's Website
In a blog post shared by ZDNet, security researcher Vishal Bharad claims that he found a bug that would have allowed a hacker to inject a virus or malicious script onto Apple's iCloud website.
According to Bharad, the vulnerability consisted of creating a Pages or Keynote document on the iCloud website with the name field containing the XSS payload. Sharing the document with another...
Latest Chrome 88 Update Includes Important Fix for Zero-Day Vulnerability
Google has released Chrome version 88.0.4324.150 with an important fix for a zero-day vulnerability in the web browser that the company says is likely to have been exploited in the wild.
Google hasn't provided specific details about the heap buffer overflow memory corruption bug known as CVE-2021-21148, and says it won't do so "until a majority of users are updated with a fix."
However, ZDNe...
Root Access Sudo Bug Found to Affect macOS Big Sur
A sudo bug that can grant an attacker root access has been discovered to affect macOS Big Sur (via ZDNet).
The security vulnerability, identified last week as "CVE-2021-3156" by the Qualys Security Team, affects sudo, which is a program that allows users to run commands with the security privileges of another user, such as an administrator. The bug triggers a "heap overflow" in sudo that...
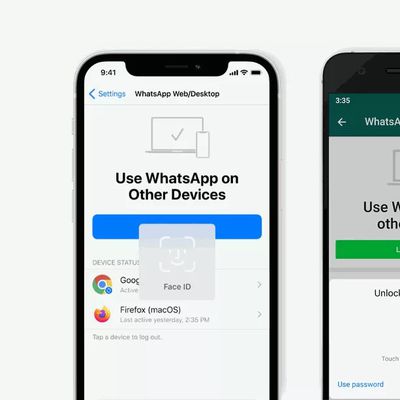
WhatsApp to Require Face ID or Touch ID When Linking Accounts to Web and Desktop Apps
WhatsApp will soon require biometric authentication to link a WhatsApp account to a computer web browser or desktop app, reports The Verge.
The mobile app uses a QR code to link a user account to a web browser or desktop app, but the company wants to make the process more secure so that it can't be done by anyone who happens to gain access to your iPhone.
The new system will be enabled by ...

Many iOS Encryption Measures 'Unused,' Say Cryptographers
iOS does not utilize built-in encryption measures as much as it could do, allowing for potentially unnecessary security vulnerabilities, according to cryptographers at Johns Hopkins University (via Wired).
Using publicly available documentation from Apple and Google, law enforcement reports about bypassing mobile security features, and their own analysis, the cryptographers assessed the...

Nest to Require Two-Factor Authentication for All Accounts From This Month
Google will require compulsory use of two-factor authentication for all Nest accounts starting this month, the company has announced.
In other words, users who haven't already enabled smartphone-based 2FA or migrated to a Google account will have to verify their identity via email-based authentication every time they log in. The change was spotted by Engadget in an updated Nest help page:
E...












