Root Access Sudo Bug Found to Affect macOS Big Sur
A sudo bug that can grant an attacker root access has been discovered to affect macOS Big Sur (via ZDNet).
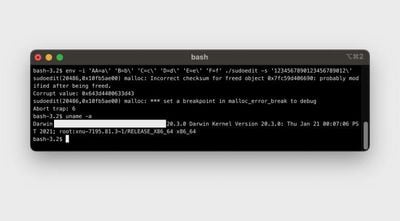
The security vulnerability, identified last week as "CVE-2021-3156" by the Qualys Security Team, affects sudo, which is a program that allows users to run commands with the security privileges of another user, such as an administrator. The bug triggers a "heap overflow" in sudo that changes the current user's privileges to enable root-level access. This can give an attacker access to the entire system. An attacker would need to gain low-level access to a system first to be able to exploit the bug, such as via planted malware.
Sudo is part of many Unix-like systems, including macOS, but it was initially unknown if the vulnerability affected Mac machines since it was only tested by Qualys on Ubuntu, Debian, and Fedora. Security researcher Matthew Hickey has now confirmed that the most recent version of macOS, macOS Big Sur 11.2 can be subject to the sudo attack.
Last week, there was speculation that the macOS Big Sur 11.2 update may address the sudo vulnerability, though it was not definitively known at the time if the bug would affect macOS. While it was found that sudo was left unchanged in macOS Big Sur 11.2, it is now clear that macOS is affected by the exploit.
With some minor modifications, Hickey found that the sudo bug could be used to grant attackers access to macOS root accounts, and the discovery has now been verified by Carnegie Mellon University vulnerability analyst Will Dormann.
Apple has reportedly been notified of the CVE-2021-3156 vulnerability, and due to the severity of the issue, a patch will likely be released soon.
Popular Stories
Since the iPhone X in 2017, all of Apple's highest-end iPhone models have featured either stainless steel or titanium frames, but it has now been rumored that this design decision will be coming to an end with the iPhone 17 Pro models later this year.
In a post on Chinese social media platform Weibo today, the account Instant Digital said that the iPhone 17 Pro models will have an aluminum...
Apple is continuing to refine and update iOS 26, and beta three features smaller changes than we saw in beta 2, plus further tweaks to the Liquid Glass design. Apple is gearing up for the next phase of beta testing, and the company has promised that a public beta is set to come out in July.
Transparency
In some apps like Apple Music, Podcasts, and the App Store, Apple has toned down the...
In select U.S. states, residents can add their driver's license or state ID to the Wallet app on the iPhone and Apple Watch, providing a convenient and contactless way to display proof of identity or age at select airports and businesses, and in select apps.
Unfortunately, this feature continues to roll out very slowly since it was announced in 2021, with only nine U.S. states, Puerto Rico,...
Apple will launch its new iPhone 17 series in two months, and the iPhone 17 Pro models are expected to get a new design for the rear casing and the camera area. But more significant changes to the lineup are not expected until next year, when the iPhone 18 models arrive.
If you're thinking of trading in your iPhone for this year's latest, consider the following features rumored to be coming...
Apple is expanding the ability to add an Apple Account Card to the Wallet app to more countries, according to backend Apple Pay changes.
With iOS 15.5, Apple updated the Wallet app to allow users to add an Apple Account Card, which displays the Apple credit balance associated with an Apple ID.
If you receive an Apple gift card, for example, it is added to an Apple Account that is also...
Three out of four iPhone 17 models will feature more RAM than the equivalent iPhone 16 models, according to a new leak that aligns with previous rumors.
The all-new iPhone 17 Air, the iPhone 17 Pro, and the iPhone 17 Pro Max will each be equipped with 12GB of RAM, according to Fixed Focus Digital, an account with more than two million followers on Chinese social media platform Weibo. The...
Apple should unveil the iPhone 17 series in September, and there might be one bigger difference between the Pro and Pro Max models this year.
As always, the Pro Max model will be larger than the Pro model:iPhone 17 Pro: 6.3-inch display
iPhone 17 Pro Max: 6.9-inch displayGiven the Pro Max is physically larger than the Pro, it has more internal space, allowing for a larger battery and...
The calendar has turned to July, meaning that 2025 is now more than half over. And while the summer months are often quiet for Apple, the company still has more than a dozen products coming later this year, according to rumors.
Below, we have outlined at least 15 new Apple products that are expected to launch later this year, along with key rumored features for each.
iPhone 17 Series
iPho...