Security
By MacRumors Staff
Security How Tos
How to Check iCloud Keychain Password Security
Using iCloud Keychain, Apple's Safari browser stores and syncs all the passwords you use for different websites and apps through iCloud. And in iOS 14 and later, Apple provides security recommendations that warn you if a password you're using is putting your accounts at risk.
Safari securely monitors your saved passwords using strong cryptographic techniques, and regularly checks derivations ...
Read Full Article

How to Use Firefox Private Network to Encrypt Your Web Traffic
Mozilla this week began piloting its own browser-based VPN service, and if you're located in the U.S. you can start testing it for free right away.
Called the Firefox Private Network, the service promises Firefox users a more secure, encrypted path to the web that prevents eavesdroppers from spying on your browsing activity and hides your location from websites and ad trackers.
In that...

How to Encrypt a USB Flash Drive in macOS Mojave
In macOS Mojave, you can choose to encrypt and decrypt disks on the fly right from the desktop. Using this convenient Finder option, we're going to show you how to encrypt a USB flash drive (or "thumb drive"), which is useful if you're traveling light and want to take sensitive data with you for use on another Mac.
Finder uses XTS-AES encryption, the same encryption that FileVault 2 uses to...
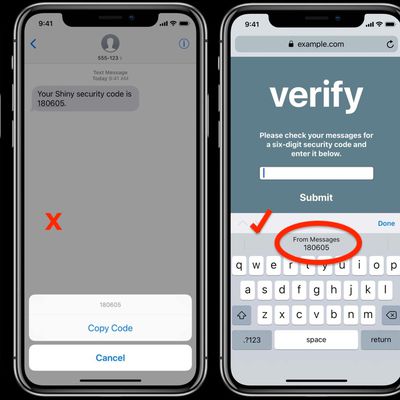
How to Use Secure Code AutoFill in iOS 12 and macOS Mojave
Most readers will have at some point received a two-factor authentication code delivered to them by SMS text message. Many apps and websites send the one-time codes to confirm that the person attempting to log in to an account is the legitimate account holder, and not just someone using a stolen password.
Depending on how notifications are set up on your iPhone, receiving a code via text...
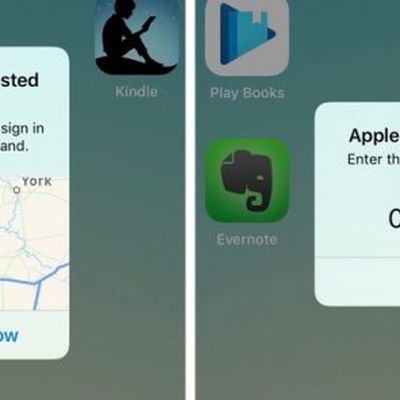
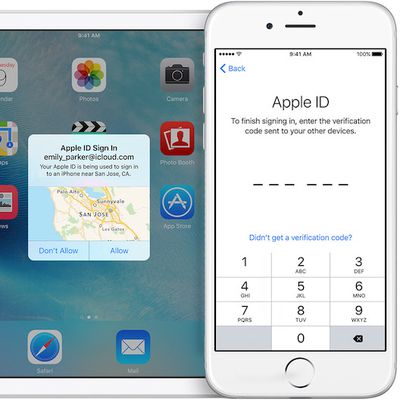
How to Secure Your Apple ID Using Two-Factor Authentication
Apple introduced two-factor authentication (2FA) in 2015 to provide an enhanced level of security when accessing Apple ID accounts. With 2FA enabled, you'll be the only person who can access your account, regardless of whether someone learns your password – as the result of a hack or a phishing scam, for example – so it's well worth taking the time to enable the feature. In this article,...
Security Articles

Over 500,000 Zoom Accounts Sold on the Dark Web and Hacker Forums
Hundreds of thousands of Zoom accounts are being sold or given away for free on the dark web and hacker forums, according to a new report by BleepingComputer.
Zoom has surged in popularity in recent weeks as the number of people working from home has increased, but concerns about the videoconferencing app's security have also made the headlines. However, the availability of Zoom accounts on...

Zoom Accused of Misleading Users With 'End-to-End Encryption' Claims Amid Other Security Issues [Updated]
Zoom is facing fresh scrutiny today following a report that the videoconferencing app's encryption claims are misleading.
Zoom states on its website and in its security white paper that the app supports end-to-end encryption, a term that refers to a way of protecting user content so that the company has no access to it whatsoever.
However, an investigation by The Intercept reveals that...

Israel Passes Emergency Law to Track and Trace Mobile Users With Suspected COVID-19
Israel has passed emergency measures that will allow security agencies to track the smartphone data of people with suspected COVID-19 and find others they may have come into contact with (via BBC News).
The Israeli government said the new powers will be used to identify people infected with coronavirus and make sure they're following quarantine rules.
On Monday, an Israeli parliamentary...
iPhones Can Now Be Used to Generate 2FA Security Keys for Google Accounts
A new update to Google's Smart Lock iOS app lets users set up their iPhone or iPad as a security key for two-factor authentication when signing into native Google services via Chrome browser.
Once the feature is set up in the app, attempting to log in to a Google service via Chrome on another device such as a laptop results in a push notification being sent to their iOS device.
The user...
'Turkish Crime Family' Hacker Pleads Guilty to Blackmailing Apple
A 22-year-old man who claimed to be the spokesman for a hacker group called the "Turkish Crime Family" has pleaded guilty in London to trying to blackmail Apple, reports Bloomberg.
In March 2017, Kerem Albayrak claimed to have access to several million iCloud accounts and demanded that Apple pay $75,000 in cryptocurrencies, or he would reset a number of the accounts and make the database...
Google Pixel 4's Face Unlock Feature Works With Eyes Closed, Sparking Security Concerns
Google has ignited security concerns over the facial authentication system in its new Pixel 4 smartphone by admitting that it will unlock the device even when the user's eyes are shut.
Google unveiled the Pixel 4 this week to mostly positive reviews, many of which praised the phone for its super-fast new face unlock system, which replaces the fingerprint sensor and works much the same as...

Israeli Security Firm Claims Spyware Tool Can Harvest iCloud Data in Targeted iPhone Attack
An Israeli security firm claims it has developed a smartphone surveillance tool that can harvest not only a user's local data but also all their device's communications with cloud-based services provided by the likes of Apple, Google, Amazon, and Microsoft.
According to a report from the Financial Times [paywalled], the latest Pegasus spyware sold by NSO Group is being marketed to potential...

Serious Vulnerability in Zoom Video Conference App Could Let Websites Hijack Mac Webcams [Updated]
A serious zero-day vulnerability in the Zoom video conferencing app for Mac was publicly disclosed today by security researcher Jonathan Leitschuh.
In a Medium post, Leitschuh demonstrated that simply visiting a webpage allows the site to forcibly initiate a video call on a Mac with the Zoom app installed.
The flaw is said to be partly due to a web server the Zoom app installs on Macs...

Data Extraction Company Cellebrite Touts New Software for Cracking iPhones and iPads Running up to iOS 12.3
Israel-based software developer Cellebrite, known for breaking into mobile devices like the iPhone to obtain sensitive data, has announced that it can now unlock any iOS device running up to iOS 12.3, which was released only a month ago.
The firm revealed the capability in a tweet posted late Friday advertising UFED Premium, the latest version of its Universal Forensic Extraction Device....

Apple and Other Tech Giants Condemn GCHQ Proposal to Eavesdrop on Encrypted Messages
Apple and other tech giants have joined civil society groups and security experts in condemning proposals from Britain's cybersecurity agency that would enable law enforcement to access end-to-end encrypted messages (via CNBC).
British Government's Communications HQ in Cheltenham, Gloucestershire
In an open letter to the U.K.'s GCHQ (Government Communications Headquarters), 47 signatories...

CES 2019: Arlo Unveils HomeKit-Enabled Ultra 4K HDR Security Camera and All-in-One Home Security System
Arlo Technologies today announced its new Arlo Ultra 4K wire-free HDR security camera and Arlo Security System, the latter of which is being billed as a comprehensive security solution for the home or business.
The HomeKit-compatible Arlo Ultra 4K HDR video camera features both color and black and white night vision via an LED integrated spotlight, a 180-degree panoramic field-of-view lens, ...

Australia Passes Controversial Encryption Bill Despite Opposition From Apple and Other Tech Companies
The Australian parliament on Thursday passed controversial encryption legislation that could result in tech companies being forced to give law enforcement access to encrypted customer messages.
As we reported in October, Apple opposed the legislation in a seven-page letter to the Australian parliament, calling the encryption bill "dangerously ambiguous" and wide open to potential abuse by...
Complex Passcode Bypass Method Exposes iPhone Contacts and Photos in iOS 12
A passcode bypass vulnerability has been discovered in iOS 12 that potentially allows an attacker to access photos and contact details on a locked iPhone.
The rather convoluted bypass method was shared in a video by Jose Rodriguez, who has discovered iOS bugs in the past that Apple has subsequently fixed.
With physical access to the locked device, the attacker first asks Siri to activate ...
British Airways Website and Mobile App Suffer Huge Customer Data Breach
British Airways says it is investigating the theft of customer data from its website and mobile app over a two-week period, during which 380,000 payment cards were exposed (via The Guardian).
"From 22:58 BST August 21 2018 until 21:45 BST September 5 2018 inclusive, the personal and financial details of customers making bookings on our website and app were compromised," the airline revealed in ...
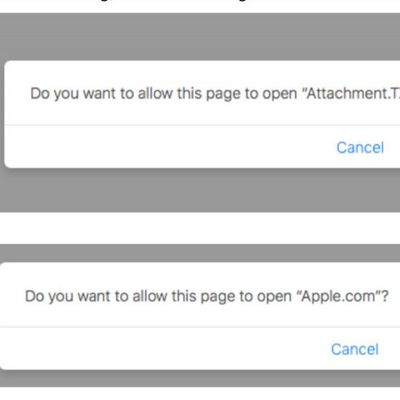
Security Researcher Shows How Remote macOS Exploit Hoodwinks Safari Users With Custom URL Schemes
A security researcher has demonstrated how macOS users are vulnerable to remote infection through a malicious exploit involving the "Do you want to allow..." popup that can be encountered when visiting websites in Safari.
In a lengthy breakdown, Patrick Wardle explains how the exploit utilizes document handlers, which request permission to open a link or a file in another app – like a PDF in ...

Timehop Service Suffers Data Breach Affecting 21 Million Users [Updated]
The company behind social media app Timehop has revealed its servers suffered a data breach in which the personal details of around 21 million users were stolen.
The company, whose service integrates with users' social media accounts to display photos and memories they may have forgotten about, said it became aware of the attack as it was happening in the early hours of July 4.
In a stateme...

ElcomSoft's Latest Tool Can Allegedly Access iMessages in iCloud, But Only in Extreme Circumstances
Russian company ElcomSoft today claimed that the latest version of its Phone Breaker software can remotely access iMessage conversation histories stored in iCloud, although there are several strings attached.
Namely, the person attempting to extract iMessages from an iCloud account would need the following before being able to do so:Elcomsoft Phone Breaker version 8.3
The associated Apple...
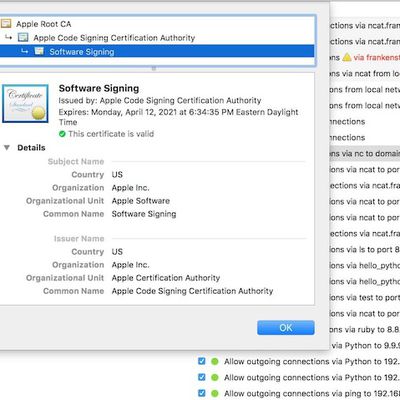
Third-Party macOS Security Tools Vulnerable to Malware Code-Signing Bypasses for Years
Hackers have had an "easy way" to get certain malware past signature checks in third-party security tools since Apple's OS X Leopard operating system in 2007, according to a detailed new report today by Ars Technica. Researchers discovered that hackers could essentially trick the security tools -- designed to sniff out suspiciously signed software -- into thinking the malware was officially...

Thousands of Apple ID Passwords Leaked by Teen Phone Monitoring App Server
ZDNet reports that a server used by an app for parents to monitor their teenagers' phone activity has leaked tens of thousands of login credentials, including the Apple IDs of children.
The leaked data belonged to customers of TeenSafe, a "secure" monitoring app for iOS and Android that allows parents to view their child's text messages and location, call history, web browsing history, and...
LocationSmart Bug Provided Easy Access to Real-Time Location Data of Millions of Phones
Robert Xiao, a computer science student at Carnegie Mellon, recently discovered a vulnerability in LocationSmart's website that made the real-time location of millions of phones readily available to anyone with the knowhow.
For background, LocationSmart is a company that collects location data of mobile customers from major carriers, including Verizon, AT&T, Sprint, and T-Mobile in the...












