Apple Security
By MacRumors Staff
Apple Security Reviews

Review: Yubico's 5C NFC YubiKey Works Well With Apple's Security Keys Feature
With the launch of iOS 16.3 and macOS 13.2 Ventura, Apple added Security Keys for the Apple ID, offering a more robust way to protect your Apple account and everything associated with your Apple account.
A Security Key is a physical device that works with two-factor authentication. Instead of using a code generated by a secondary Apple device for authentication, when you log into your Apple...
Read Full Article (122 comments)
Apple Security How Tos
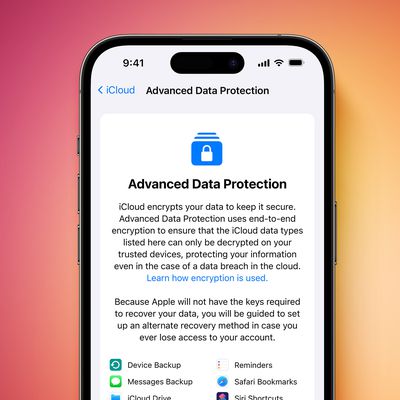
Enable End-to-End Encryption for Your iCloud Backups
Apple's Advanced Data Protection for iCloud feature uses end-to-end encryption to provide the highest level of cloud data security that Apple offers. Here's everything you need to know about enabling it on your devices.
The encrypted security feature gives you the choice to further protect your important iCloud data, including iCloud Backup, Photos, Notes, and more.
Apple's use of...
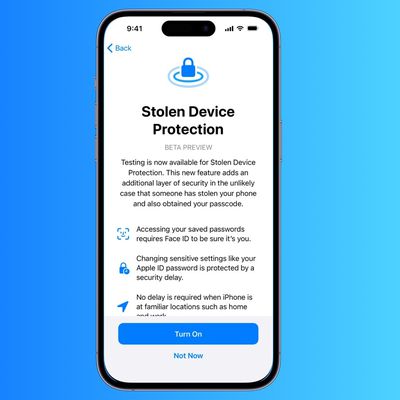
How to Enable Stolen Device Protection on iPhone
When Apple released iOS 17.3 in January, it introduced a Stolen Device Protection feature to provide iPhone users with added security. This article explains what it does, why you might want to turn it on, and how to go about doing so.
In 2023, reports began emerging about a new method thieves were using to steal iPhones and access users' highly sensitive data. Thieves would surreptitiously...

iPhone Displays Green and Orange Dots: What Do They Mean?
Digital privacy is a perennial hot topic these days, and Apple is regarded as being at the forefront of security when it comes to smartphone and tablet operating systems. For example, for an app to access your iPhone or iPad's camera, camera and microphone access must be enabled for the app in question in the Settings app.
Social media apps will often ask you for access to your device's...

How to Share Passwords Among a Group on iPhone and iPad
In iOS 17 and iPadOS 17, Apple has added the ability to securely share passwords and passkeys with people in your contacts using a new shared password function. It's called Family Passwords, and here's how to use it.
Family Passwords allows you to create a group of trusted contacts that you can share passwords and passkeys with across devices. (Passkeys let users sign in to apps and sites...

How to Unlock Your iPhone If You Forget Your New Passcode
In iOS 17, if you change your iPhone's passcode and forget it soon after, Apple offers you a 72-hour grace period to fix it without getting locked out of your device. Here's how it works.
In iOS 17 and iPadOS 17, it is now possible to reset an iPhone or iPad's new passcode with the previous passcode you used for up to three days after the change is made. In other words, Apple lets you use...

How to Share Passwords With Friends and Family on iPhone and iPad
In iOS 17 and iPadOS 17, Apple has added the ability to securely share passwords and passkeys with friends and family members using a new shared password function. Here's how to use it.
Family Passwords allows you to create a group of trusted contacts that you can share passwords and passkeys with across devices. (Passkeys let users sign in to apps and sites the same way they unlock their...
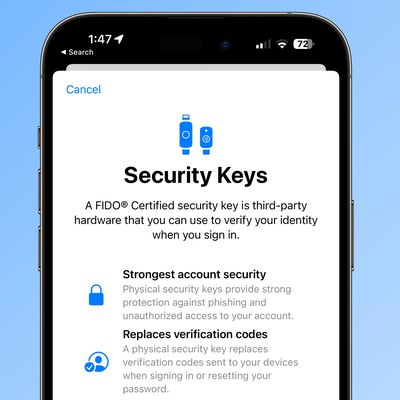
How to Protect Your Apple ID With Security Keys
Apple has introduced security keys as an additional step to help users protect their Apple ID accounts. Keep reading to learn why the alternative authentication method is the most secure method available and what you need to do to set it up.
What Are Security Keys?
With the release of iOS 16.3, iPadOS 16.3, and macOS Ventura 13.2, Apple introduced support for security keys, or physical...

How to Set Up a Stronger Passcode on Your iPhone
Your iPhone's passcode is the first line of defense when it comes to protecting your private data. Here's how to set up a stronger one than the default six-digit passcode that you're likely already using.
If someone with malicious intentions finds out the passcode for your iPhone, they could end up causing you all sorts of trouble. With passcode access to your iPhone's contents, they could...

How to Set Up and Use the Built-in 2FA Code Generator in iOS
With online account hacking becoming increasingly widespread, all users should make sure they're taking every security measure available to them. If you use Apple devices, consider using Apple verification codes to protect your accounts. Keep reading to learn how it works.
One of the best ways to protect any online account is by using two-factor authentication (2FA). 2FA offers hardened...
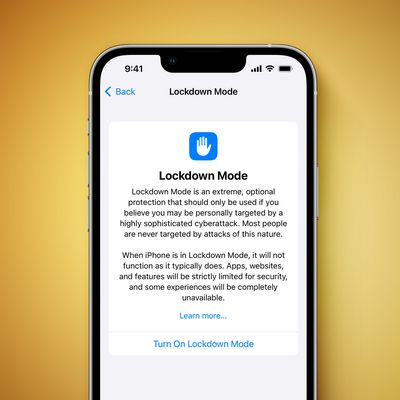
How to Enable Lockdown Mode for Heightened Security on iPhone and iPad
With the release of iOS 16 and iPadOS 16, Apple introduced Lockdown Mode, offering users an "extreme" level of security. This article explains who Lockdown Mode is for, what it does, and how to enable it.
In iOS 16 and iPadOS 16, Apple brought iPhone and iPad users Lockdown Mode, an optional new security feature that's designed to protect users who may be at risk of highly targeted...

How to Use Automatic Strong Passwords and Password Auditing in iOS 12
In iOS 12, Apple has introduced new password-related features that are designed to make it easier for iPhone and iPad users to create strong, secure, and unique passwords for app and website logins. In this guide, we'll show you how to use two of those features: automatic strong passwords and password auditing.
Automatic strong passwords ensures that if you're prompted by a website or app...
Apple Security Articles

Apple Warns More Users About Mercenary Spyware Attacks
Apple this week sent out notices to people who may have been targeted with government-sponsored spyware attacks, reports TechCrunch. An Italian journalist and a Dutch activist said that they received notifications from Apple via iMessage and email.
Apple detected that you are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your...

UK Court Rejects Government Secrecy in Apple's Fight Against Backdoor Request
Apple has filed a legal appeal against a UK government order requiring the company to create a "back door" to its encrypted cloud storage systems, the Investigatory Powers Tribunal (IPT) confirmed on Monday (via Reuters). The confirmation means that the Home Office cannot keep all the details of its demand out of the public domain.
The high-profile challenge follows reports earlier this year ...

US Probes UK's Apple Encryption Demand for Possible Treaty Violation
U.S. officials are looking at whether the United Kingdom violated a bilateral agreement by demanding Apple create a "backdoor" to access end-to-end encrypted iCloud data, according to a letter from National Intelligence Director Tulsi Gabbard (via Reuters).
The investigation comes after Apple's recent decision to withdraw its Advanced Data Protection feature from the UK after the British...

Apple's Data Encryption Changes in the UK Explained
Apple on February 21 withdrew its Advanced Data Protection feature from the United Kingdom following government demands for backdoor access to encrypted user data. The move came after UK officials reportedly ordered Apple in secret to provide unrestricted access to encrypted iCloud not just in the UK, but worldwide.
The development has naturally left some Apple device users in the UK asking ...

Apple Pulls Encrypted iCloud Security Feature in UK Amid Government Backdoor Demands
Apple has withdrawn its Advanced Data Protection iCloud feature from the United Kingdom following government demands for backdoor access to encrypted user data, according to Bloomberg. The move comes after UK officials secretly ordered Apple to provide unrestricted access to encrypted iCloud content worldwide.
Customers who are already using Advanced Data Protection, or ADP, will need to...

US Lawmakers Urge Intelligence Chief to Fight UK iCloud Backdoor Order
Members of key congressional oversight committees have called on the United States' new top intelligence director to pressure the United Kingdom to withdraw its controversial demand for Apple to create a backdoor into encrypted user data stored in iCloud, according to The Washington Post.
Last week The Post revealed that a secret UK order, issued under the Investigatory Powers Act last...

Could Apple Pull iCloud Services From the UK Market?
Given today's bombshell report revealing the UK government's unprecedented demand for backdoor access to encrypted iCloud data, it's clear that Apple now faces a massive challenge. How it responds could have major implications for not only the company's privacy stance, but also its global operations as well as its reputation.
According to The Washington Post, the British government has...

Apple Ordered by UK to Create Global iCloud Encryption Backdoor
The British government has secretly demanded that Apple give it blanket access to all encrypted user content uploaded to the cloud, reports The Washington Post.
The undisclosed order is said to have been issued last month, and requires that Apple creates a back door that allows UK security officials unencumbered access to encrypted user data worldwide – an unprecedented demand not before...

Apple Warns Users in 92 Countries About Mercenary Spyware Attacks
Apple on Wednesday sent threat notifications to users in 92 countries warning that they may have been targeted by mercenary spyware attacks, likely because of who they are or what they do.
According to TechCrunch, Apple sent the alerts to the individuals at 12 p.m. Pacific Time, delivered via email and iMessage using the contact details associated with the user's Apple ID. A notification...

Apple Silicon Vulnerability Allows Hackers to Extract Encryption Keys
An unpatchable vulnerability has been discovered in Apple's M-series chips that allows attackers to extract secret encryption keys from Macs under certain conditions, according to a newly published academic research paper (via ArsTechnica).
Named "GoFetch," the type of cyber attack described involves Data Memory-Dependent Prefetchers (DMPs), which try to predict what data the computer will...

Apple Warns Proposed UK Law Could 'Secretly Veto' Global User Protections
Apple is "deeply concerned" that proposed changes to British surveillance legislation could give the U.K. government unprecedented powers to secretly prevent software updates from being released in any other country (via BBC News).
The UK government is planning to update the Investigatory Powers Act (IPA), which came into effect in 2016 and allows the British Home Office to outlaw certain...

Research Reveals How iPhone Push Notifications Leak User Data
Security researcher Tommy Mysk has demonstrated that iPhone push notifications are being used by popular apps to covertly send data about the user.
In a new video outlining the practice, Mysk highlighted how certain iOS apps exploit a feature introduced in iOS 10 that is designed to allow apps to customize push notifications. This feature, initially intended to enable apps to enrich...

Apple Wins Early Victory Against Spyware Maker NSO Group in Court
Apple has dealt a blow against spyware maker NSO Group and the Israeli firm's efforts to move Apple's lawsuit against it to its home country. Apple in November 2021 sued the group and its parent company with the aim of holding it accountable for targeting Apple users with spyware used for surveillance purposes.
Judge Donato denied NSO's motion to dismiss Apple's case "in all respects," and...

Apple Silicon Security Flaw Discovered in iPhone 12 and M2 MacBook Air
A security vulnerability that could allow attackers to access sensitive data has been discovered in some Apple silicon GPUs.
A recent investigation by cybersecurity firm Trail of Bits discovered the security flaw, named "LeftoverLocals," which allows attackers with local access to a device to retrieve data processed in the GPU's local memory. The issue is particularly concerning because of...
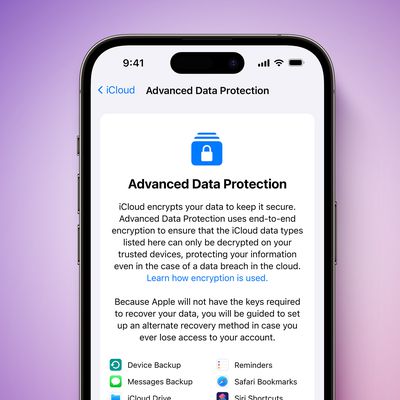
Apple Promotes iCloud's Advanced End-to-End Encryption Feature as Data Breaches Increase
Apple today shared a study conducted by MIT professor Dr. Stuart Madnick that found 2.6 billion personal records were compromised by data breaches in the past two years. The study was commissioned by Apple, but the cover page says that the "conclusions and opinions expressed are exclusively those of the author."
Apple provided an overview of the study in its press release:The report...

Apple Shares New 'The Underdogs' Video Focusing on Apple Security Features at Work
Apple today shared a humorous new video on its YouTube channel that dramatizes many of the security features available when using Apple products at work.
Titled "Swiped," the spot opens with a design team that is shortly about to give a "game-changing" presentation to a client, only for the MacBook Air on which the presentation exists to be swiped by thieves in the street when the team...

Apple Responds to Report About Thieves Spying on iPhone Passcodes to 'Steal Your Entire Digital Life'
An in-depth report published today by The Wall Street Journal's Joanna Stern and Nicole Nguyen highlights instances of thieves spying on a victim's iPhone passcode before stealing the device in order to gain access to the device, data, and money.
All of the victims interviewed said their iPhones were stolen while they were out socializing at bars and other public places at night. Some...
Apple Launches New Security Research Website
Apple today introduced Apple Security Research, a new website that is dedicated to improving the methods available to security researchers for reporting issues to Apple. The site offers up tools for sending Apple security reports, getting real-time status updates, and communicating with Apple engineers.
In addition to housing information on the Apple Security Bounty program, the website is a ...
PSA: Safari Security Flaw 'Actively Exploited,' Update Your Apple Devices Now
This week, Apple released critical software updates for Safari which fix a security flaw that exists in the browser across iPhone, iPad, and Mac platforms. Here's what you need to know.
Specifically, the platform-wide fix is for a vulnerability in Safari's WebKit engine that Apple believes may have been "actively exploited" in the wild by hackers.
The flaw, according to Apple, could...

Apple Apologizes to Researcher for Ignoring iOS Vulnerabilities, Says It's 'Still Investigating'
Last week, security researcher Denis Tokarev made several zero-day iOS vulnerabilities public after he said that Apple had ignored his reports and had failed to fix the issues for several months.
Tokarev today told Motherboard that Apple got in touch after he went public with his complaints and after they saw significant media attention. In an email, Apple apologized for the contact delay...











