Zoom
By MacRumors Staff
Zoom Articles
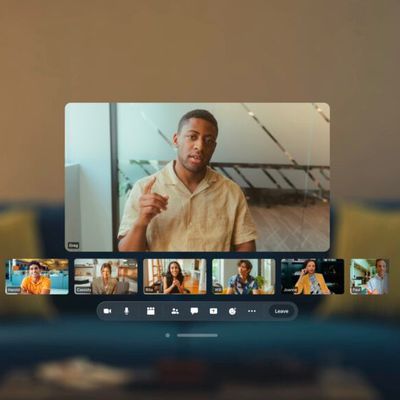
Zoom Shows Off Immersive New Vision Pro App With Personas, 3D Object Sharing and More
With the launch of the Vision Pro just days away, popular video collaboration service Zoom announced a Vision Pro app that is set to come out on Friday, February 2. The Zoom app for Vision Pro is meant to blur the lines of in-person and remote meetings to help teams feel more connected with one another.
The Zoom app will work on the "infinite canvas" of the Vision Pro, with the scalable...
Read Full Article 100 comments
Zoom Updates Mac App With Important Security Fix
Zoom has released a new version of its macOS app with a fix for a security vulnerability affecting the app's automatic updates feature.
In an August 13 security bulletin, Zoom said version 5.7.3 to version 5.11.3 of its macOS app contain a vulnerability in the auto-update process that can be exploited by a local low-privileged user to gain root privileges to the operating system. The...
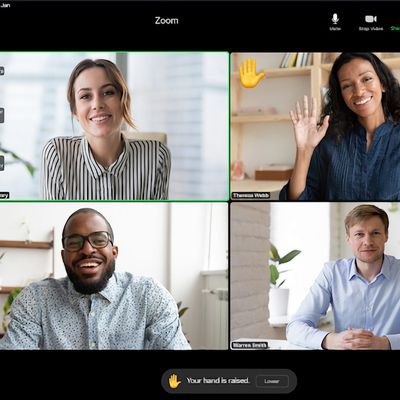
Zoom Updated With 'Raise Hand' and 'Thumbs Up' Gesture Recognition on iPad
Zoom today announced the latest version of its popular video conferencing app, and one of the key new features is gesture recognition on the iPad, enabling users to use visual gestures to automatically use a corresponding meeting reaction.
The feature currently supports the "Raise Hand" and "Thumbs Up" reactions. If you raise your hand or give a thumbs up in real life, a hand or thumbs up...
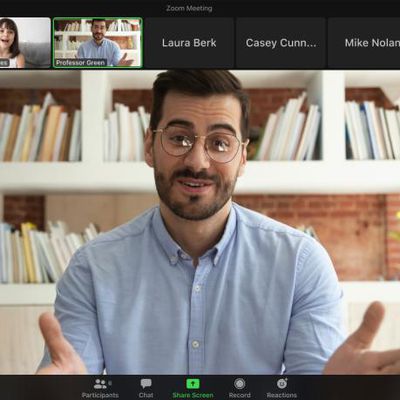
Zoom Gains Focus Mode to Help Reduce Distractions in Virtual Classrooms
Zoom has introduced a new feature called Focus Mode that's designed to prevent students from distracting each other during virtual classrooms.
When enabled, Focus Mode allows the teacher or lecturer taking the class to see all the students, while each student can only see the teacher.
The setting can be activated at any time by the teleconferencing host, so for example it could be...
Zoom to Pay $85 Million to Users for Misleading Encryption Claims
As part of a class action lawsuit settlement, Zoom says it will pay $85 million to users for misleading them about offering end-to-end encryption on its videoconferencing service.
According to ArsTechnica, the company was accused of lying about its encryption description on its website and in a security white paper, as well as providing user data to Facebook and Google without users'...
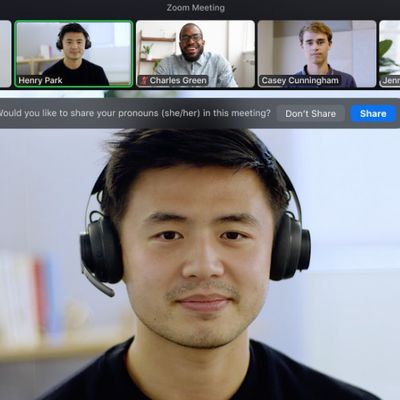
Latest Zoom Update Improves iPad Calls, Adds Custom Video Filters, Gender Pronouns, and More
Last month, Zoom added support for the new Center Stage feature exclusive to Apple's latest iPad Pro models, and this month the popular video conferencing app is back with another update containing several interface improvements and usability features on iOS.
Notable enhancements in version 5.7.0 of the app include a better iPad "visual experience", support for individual call participants...
Zoom Adds Support for iPad Pro's New Center Stage Feature
The Zoom app for iOS was today updated to introduce support for the latest iPad Pro models, with the new software adding integration with the Center Stage feature.
Apple's 2021 iPad Pro models include a front-facing "Center Stage" Ultra Wide camera function that uses machine learning to automatically detect people in the frame, panning and zooming to keep them in view during FaceTime...
Apple Gave Zoom Access to Special API to Use iPad Camera During Split View Multitasking
Zoom, a hallmark platform used by millions during the global health crisis, has been given access to a special iPadOS API that allows the app to use the iPad camera while the app is in use in Split View multitasking mode.
This case of special treatment was first brought to attention by app developer Jeremy Provost, who, in a blog post, explains that Zoom uses a special API that allows the...

Zoom With Support for Apple Silicon Set to Launch Today
Popular videoconferencing app Zoom is due to be updated with native support for Apple Silicon Macs today.
A Zoom support document, spotted by 9to5Mac, contains release notes for an update scheduled to be released today. The most notable update is support for Apple Silicon processors, and Zoom will release a separate installer for the app on Apple Silicon Macs.
The update also...
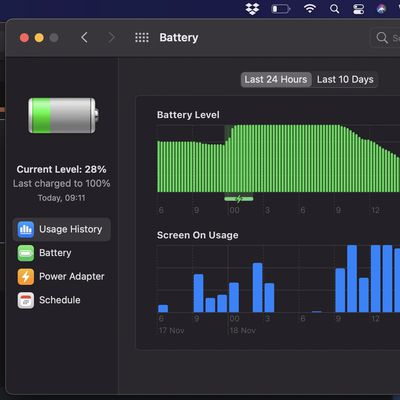
Zoom Video Calls Drain Apple M1 MacBook Air Battery by Only 10-13% Per Hour
As more customers get their hands on the first Apple Silicon Macs, we continue to see some interesting performance and battery life tests surface based on real-world usage situations, with the latest including Zoom video calling.
MacRumors forum member "acidfast7_redux," who resides in the UK, spent most of their work day today on Zoom video calls using their new MacBook Air with the M1 chip ...

Zoom Now Says End-to-End Encryption Will Be Available for All Users
In a U-turn by the popular videoconferencing platform, Zoom this week announced it will make end-to-end encryption available to all users, both paid and unpaid.
...we have identified a path forward that balances the legitimate right of all users to privacy and the safety of users on our platform. This will enable us to offer E2EE as an advanced add-on feature for all of our users around the...

Zoom Developing End-to-End Encryption Feature for Paying Users
Videoconferencing service Zoom says it is developing end-to-end encryption for the platform, but the feature will only be available to paying users.
Speaking to Reuters, Zoom security consultant Alex Stamos confirmed the plan, which had been based on "a combination of technological, safety and business factors."
Zoom has attracted millions of free and paying customers amid the global...

Over 500,000 Zoom Accounts Sold on the Dark Web and Hacker Forums
Hundreds of thousands of Zoom accounts are being sold or given away for free on the dark web and hacker forums, according to a new report by BleepingComputer.
Zoom has surged in popularity in recent weeks as the number of people working from home has increased, but concerns about the videoconferencing app's security have also made the headlines. However, the availability of Zoom accounts on...
Zoom Updates Mac App Installer to Remove Controversial 'Preflight' Installation Method
The popular video conferencing company Zoom has been under scrutiny over the past few days for the method used to install the Mac version of its app, which essentially abused a "preflight" compatibility check to install the app without the user needing to explicitly grant installation permission, as highlighted by developer Felix Seele earlier this week.
Screenshot of preflight compatibility ...

Apple Pushes Another Automatic Mac Software Update to Address Further Zoom-Related Vulnerabilities
Apple today pushed a second silent security update to Macs to address further vulnerabilities related to the Zoom video conferencing app for macOS, reports The Verge.
Apple removed software that was installed by RingCentral and Zhumu, two video conferencing apps that relied on technology from Zoom and were also found to have the same vulnerabilities as Zoom earlier this week.
These two...

Apple Pushes Automatic Mac Software Update to Remove Vulnerable Zoom Web Server
Earlier this week, a serious vulnerability with the Zoom video conferencing app for macOS was disclosed, with attackers potentially able to hijack users' webcams.
The vulnerability was particularly notable because Zoom had installed a hidden web server on users' computers in order to allow for automatic answering of incoming calls, and that web server was not only the weak point that could...

Serious Vulnerability in Zoom Video Conference App Could Let Websites Hijack Mac Webcams [Updated]
A serious zero-day vulnerability in the Zoom video conferencing app for Mac was publicly disclosed today by security researcher Jonathan Leitschuh.
In a Medium post, Leitschuh demonstrated that simply visiting a webpage allows the site to forcibly initiate a video call on a Mac with the Zoom app installed.
The flaw is said to be partly due to a web server the Zoom app installs on Macs...












