A new vulnerability within iOS 11 was uncovered over the weekend, this time centering upon the QR code scanner in the iPhone camera app. With the new scanning feature in iOS 11, users can open the Camera app on iPhone or iPad, point the device at a QR code, and tap a notification to access whatever the code contains.
In a new report by Infosec, the researchers discovered that QR codes related to website links can potentially trick users by displaying an "unsuspicious" website link in the notification, while actually leading them to a completely different site. Infosec showed this off by creating a QR code that generates a notification to "Open 'facebook.com' in Safari", but then leads to its own website.
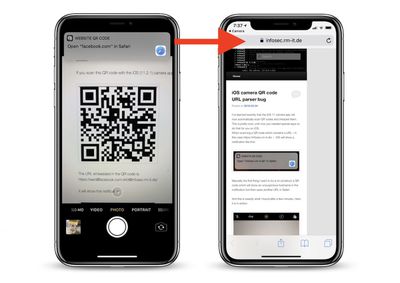
Infosec explained that the Camera app isn't properly parsing URLs in QR codes, and appears to be tricked by simply editing URLs with a few extra characters:
The URL embedded in the QR code is: https://xxx\@facebook.com:443@infosec.rm-it.de/
But if you tap it to open the site, it will instead open https://infosec.rm-it.de/
The URL parser of the camera app has a problem here detecting the hostname in this URL in the same way as Safari does. It probably detects “xxx\” as the username to be sent to “facebook.com:443”. While Safari might take the complete string “xxx\@facebook.com” as a username and “443” as the password to be sent to infosec.rm-it.de. This leads to a different hostname being displayed in the notification compared to what actually is opened in Safari.
iOS 11 has faced a number of bugs and issues since its launch last September, including one that was fixed in December that allowed unauthorized access to HomeKit devices.
Apple iOS camera app doesn't properly parse URLs in QR codes. It shows a different host in the notification than it really opens. As of now still unfixed: https://t.co/EMQk7uBQ9i pic.twitter.com/KE6EwYhj7s — @faker_ Roman (@faker_) March 24, 2018





















Top Rated Comments