Twitter Hackers Gained Access to Accounts Using Internal Tool
Several verified high profile Twitter accounts were hacked on Wednesday in a cryptocurrency scam that targeted accounts belonging to Apple, Tesla CEO Elon Musk, Amazon CEO Jeff Bezos, Microsoft CEO Bill Gates, and more.
Twitter has said it doesn't believe any passwords were stolen in the hack, which forced the company to temporarily lock all verified accounts on the platform. While the company continues to investigate the attack, a new report suggests at least one Twitter employee and possibly more were involved in the takeover.
Motherboard was able to speak to two of the alleged hackers, who claim they paid a Twitter employee to gain access to the compromised accounts using an internal tool. This tool apparently allows staff to change the email address associated with accounts, and it was this ability that allowed the security breach to take place.
Twitter on Thursday said that a "coordinated social engineering attack" had targeted some of its staff as part of the hack.
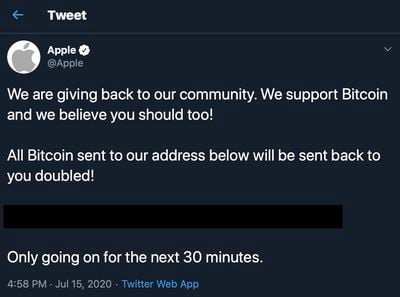
Hackers posted tweets on the compromised accounts saying that if followers sent Bitcoin to a wallet address then they would receive double the amount in return. Many users clearly fell for the scam, which earned the hackers over $100,000 in the space of two hours.
Twitter believes approximately 130 accounts were targeted by the attackers in some way as part of the incident, but the company has not yet been able to confirm whether DMs were compromised. The FBI is also investigating how the breach was allowed to happen.
Popular Stories
Apple hasn't updated the AirPods Pro since 2022, and the earbuds are due for a refresh. We're counting on a new model this year, and we've seen several hints of new AirPods tucked away in Apple's code. Rumors suggest that Apple has some exciting new features planned that will make it worthwhile to upgrade to the latest model.
Subscribe to the MacRumors YouTube channel for more videos.
Heal...
Chase this week announced a series of new perks for its premium Sapphire Reserve credit card, and one of them is for a pair of Apple services.
Specifically, the credit card now offers complimentary annual subscriptions to Apple TV+ and Apple Music, a value of up to $250 per year.
If you are already paying for Apple TV+ and/or Apple Music directly through Apple, those subscriptions will...
Popular accessory maker Anker this month launched two separate recalls for its power banks, some of which may be a fire risk.
The first recall affects Anker PowerCore 10000 Power Banks sold between June 1, 2016 and December 31, 2022 in the United States. Anker says that these power banks have a "potential issue" with the battery inside, which can lead to overheating, melting of plastic...
In 2020, Apple added a digital car key feature to its Wallet app, allowing users to lock, unlock, and start a compatible vehicle with an iPhone or Apple Watch. The feature is currently offered by select automakers, including Audi, BMW, Hyundai, Kia, Genesis, Mercedes-Benz, Volvo, and a handful of others, and it is set to expand further.
During its WWDC 2025 keynote, Apple said that 13...
Apple's next-generation iPhone 17 Pro and iPhone 17 Pro Max are around three months away, and there are plenty of rumors about the devices.
Apple is expected to launch the iPhone 17, iPhone 17 Air, iPhone 17 Pro, and iPhone 17 Pro Max in September this year.
Below, we recap key changes rumored for the iPhone 17 Pro models:Aluminum frame: iPhone 17 Pro models are rumored to have an...
Apple last month announced the launch of CarPlay Ultra, the long-awaited next-generation version of its CarPlay software system for vehicles.
There was news this week about which automakers will and won't offer CarPlay Ultra, and we have provided an updated list below.
CarPlay Ultra is currently limited to newer Aston Martin vehicles in the U.S. and Canada. Fortunately, if you cannot...
Apple will finally deliver the Apple Watch Ultra 3 sometime this year, according to analyst Jeff Pu of GF Securities Hong Kong (via @jukanlosreve).
The analyst expects both the Apple Watch Series 11 and Apple Watch Ultra 3 to arrive this year (likely alongside the new iPhone 17 lineup, if previous launches are anything to go by), according to his latest product roadmap shared with...
Apple is planning to launch a low-cost MacBook powered by an iPhone chip, according to Apple analyst Ming-Chi Kuo.
In an article published on X, Kuo explained that the device will feature a 13-inch display and the A18 Pro chip, making it the first Mac powered by an iPhone chip. The A18 Pro chip debuted in the iPhone 16 Pro last year. To date, all Apple silicon Macs have contained M-series...