The Flashback malware affecting OS X systems has gained quite a bit of publicity since it was disclosed last week that over 600,000 Macs have been infected by the malware. Flashback began life last year as a trojan and has morphed into a drive-by download taking advantage of a vulnerability in Java that Apple did not patch until last week, despite Oracle having released patches for other systems back in February.
Over the past few days, a few additional tidbits of information on Flashback have surfaced, including the arrival of some new tools to help users manage the threat.
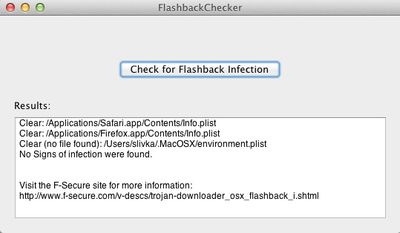
- As noted by Ars Technica, a new Mac app by the name of Flashback Checker has been released to help users determine whether their machines have been infected. Users have been instructed to use Terminal to enter commands searching for files created by the malware upon infection, and Flashback Checker offers a simple packaging of these commands behind a user interface. While the app is incredibly simple and does not offer assistance with removing Flashback if it is found on a given system, it does provide a more familiar interface for those who might be intimidated by delving into Terminal on their own.
- OpenDNS has announced that it has included filtering of Flashback in its services. OpenDNS offers a number of features to improve resolution of domain names, and the new filtering of Flashback helps prevent infection while also preventing already-infected machines from communicating with the command-and-control servers being used to deliver instructions to the infected machines.
- Forbes has an interview with Boris Sharov of Russian security firm Dr. Web, which was first to bring the magnitude of the Flashback threat to light. In the interview, Sharov describes how difficult it was to even track down the proper team at Apple with which to share their data, also noting how uncommunicative Apple has been throughout the process. In fact, the only sign of interest they've seen from Apple is the company's efforts to shut down the "sinkhole" Dr. Web was using to reroute traffic from infected machines to gauge how widespread the infections are.
“They told the registrar this [domain] is involved in a malicious scheme. Which would be true if we weren’t the ones controlling it and not doing any harm to users,” says Sharov. “This seems to mean that Apple is not considering our work as a help. It’s just annoying them.”
Sharov believes that Apple’s attempt to shut down its monitoring server was an honest mistake. But it’s a symptom of the company’s typically tight-lipped attitude. In fact, Sharov says that since Dr. Web first contacted Apple to share its findings about the unprecedented Mac-based botnet, it hasn’t received a response. “We’ve given them all the data we have,” he says. “We’ve heard nothing from them until this.”
Security experts at Kaspersky Lab, which verified Dr. Web's assessment of Flashback's prevalence, indicate that Apple is indeed taking the proper steps to address the threat, including tracking and shutting down the servers being used by the malware. But the company has little experience with threats of this magnitude and is undoubtedly scrambling to keep on top of the situation.




















