Encryption
By MacRumors Staff
Encryption How Tos
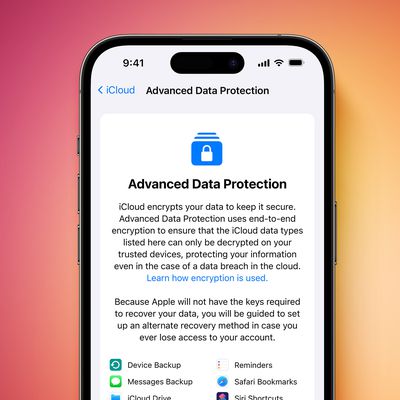
How to Enable End-to-End Encryption for iCloud Backups
With the release of iOS 16.3 and macOS 13.2, Apple is introducing Advanced Protection for iCloud, which uses end-to-end encryption to provide Apple's highest level of cloud data security yet. Here's everything you need to know about enabling it on your devices. The new security feature ensures users will have the choice to further protect their important iCloud data, including iCloud Backup, ...
Read Full Article
How to Create a New Group in Signal Encrypted Messenger
Signal Encrypted Messenger has become increasingly popular among smartphone users, thanks above all else to its emphasis on privacy and security. Signal chats are end-to-end encrypted, meaning no one – not even the Signal service – can see the messages that you send and receive to other users. In addition, Signal supports the creation of group chats, and like regular conversations in the...

How to Encrypt a USB Flash Drive in macOS Mojave
In macOS Mojave, you can choose to encrypt and decrypt disks on the fly right from the desktop. Using this convenient Finder option, we're going to show you how to encrypt a USB flash drive (or "thumb drive"), which is useful if you're traveling light and want to take sensitive data with you for use on another Mac. Finder uses XTS-AES encryption, the same encryption that FileVault 2 uses to...
Encryption Articles

Apple Silicon Vulnerability Allows Hackers to Extract Encryption Keys
An unpatchable vulnerability has been discovered in Apple's M-series chips that allows attackers to extract secret encryption keys from Macs under certain conditions, according to a newly published academic research paper (via ArsTechnica). Named "GoFetch," the type of cyber attack described involves Data Memory-Dependent Prefetchers (DMPs), which try to predict what data the computer will...
Proton Encrypted Mail Desktop App Now Available for Mac
Swiss-based privacy startup Proton today announced the availability of its end-to-end encrypted desktop mail app for macOS and Windows, with a Linux version in beta. According to the company, the Proton Mail desktop app has been optimized to integrate with Macs, which means it can sync themes with the desktop's light or dark mode, display notifications natively, and offer instant switching...

WhatsApp Working on Interoperability With Other Encrypted Messaging Apps
As part of its compliance with the EU's Digital Markets Act (DMA) legislation, WhatsApp is putting the final touches to introducing platform interoperability with other encrypted messaging apps. In September, EU lawmakers designated WhatsApp parent company Meta as one of six so-called "gatekeepers," along with Google, Amazon, Apple, ByteDance, and Microsoft, giving them six months to begin...
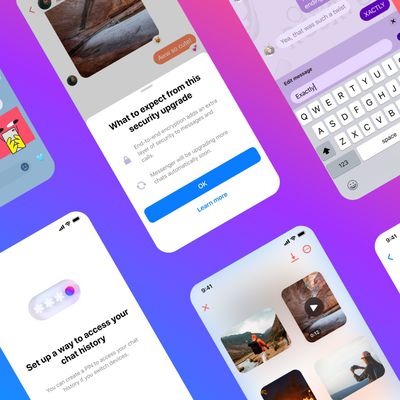
Facebook Messenger Rolls Out End-to-End Encryption by Default
Meta is rolling out end-to-end encryption for personal messages and calls on Messenger and Facebook, finally delivering on a pledge it committed to some time ago. Messenger encryption originally arrived in 2016 in the form of "secret conversations," and plans to extend the platform's cryptographic features have been floated ever since. According to Loredana Crisan, Head of Messenger,...

Proton Drive Encrypted Cloud Storage App Now Available for Mac
Swiss-based privacy startup Proton today announced the availability of its end-to-end encrypted cloud storage service for Mac users with the launch of its macOS app. Proton Drive lets users sync files between Mac and the cloud, access files offline, and free up space on local drives. Unlike iCloud, all data (including metadata) is end-to-end encrypted by default, so that no-one – not even...

Signal Tests Sharing Public Usernames in Place of Phone Numbers
Encrypted messaging app Signal has announced it is testing public account usernames so that users don't have to share their phone number to connect through the service. Currently, signing up to Signal requires that you share your phone number with other users when connecting with them. While the new method still requires an account to be associated with a number during setup, it is not...

UK Government Denies U-Turn on Plan to Scan Encrypted Messages
The UK government has denied that it has dropped a controversial plan to scan encrypted messaging services for harmful content as part of its Online Safety Bill, which is due to become law later this year. A provision in the bill allows regulator Ofcom to order messaging services to use "accredited technology" to look for and take down child sexual abuse material. However, according to a ...

Apple Provides Further Clarity on Why It Abandoned Plan to Detect CSAM in iCloud Photos
Apple on Thursday provided its fullest explanation yet for last year abandoning its controversial plan to detect known Child Sexual Abuse Material (CSAM) stored in iCloud Photos. Apple's statement, shared with Wired and reproduced below, came in response to child safety group Heat Initiative's demand that the company "detect, report, and remove" CSAM from iCloud and offer more tools for...
PSA: Google Authenticator's Cloud-Synced 2FA Codes Aren't End-to-End Encrypted
Earlier this week, Google updated its Authenticator app to enable the backup and syncing of 2FA codes across devices using a Google Account. Now an examination by Mysk security researchers has found that the sensitive one-time passcodes being synced to the cloud aren't end-to-end encrypted, leaving them potentially exposed to bad actors. Prior to the integration of Google Account support,...

WhatsApp, Other Messaging Apps Sign Open Letter Urging UK Government to Rethink 'Surveillance' Bill
WhatsApp, Signal, and other messaging services have penned an open letter to the British government appealing for it to urgently rethink the Online Safety Bill (OSB), a piece of legislation that would allow regulators to ask the platforms to monitor users in order to identify child abuse images. Under the bill, the government could force chat services to apply content moderation policies...

WhatsApp Says It Would Leave UK If Government Tried to Weaken Encryption
WhatsApp would exit the U.K. market rather than be in thrall to the government's proposed Online Safety Bill if it undermined the app's end-to-end encryption, the platform's chief has said (via BBC News). End-to-end encryption ensures that only the user and the person they are communicating with can read or listen to what is sent, and nobody in between, not even Meta/Facebook, can gain...
Proton Drive iOS and Android Apps Now Available for Encrypted Cloud Storage
Swiss-based privacy startup Proton today announced the availability of mobile apps for its Proton Drive cloud storage service, providing users with an easier way to securely upload, store, and share files from their iOS and Android devices. All files and folders uploaded to the storage service are protected by Proton's open-source, publicly-audited end-to-end encryption, which uses on-device ...

ProtonMail Unifies Encrypted Mail, Calendar, VPN, and Storage Services Under New 'Proton' Brand
Swiss-based encrypted email provider ProtonMail today announced a restructuring of its privacy-first services, bringing them under a new unifying brand name: Proton. Today, we are undertaking our biggest step forward in the movement for an internet that respects your privacy. The new, updated Proton offers one account, many services, and one privacy-by-default ecosystem. You can now enjoy...

UK Government Readies Anti-Encryption Publicity Campaign to 'Keep Children Safe' Online
The British Government is reportedly preparing a publicity attack on end-to-end encryption in an effort to mobilize public opinion against the technology by framing it as a child safety issue, with its main aim being to derail Facebook's plan to end-to-end encrypt its Messenger platform. According to Rolling Stone, the Home Office has hired the M&C Saatchi advertising agency to plan the...
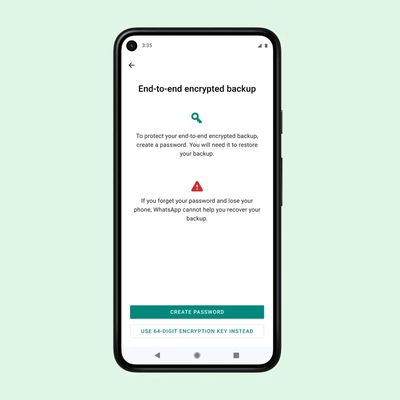
WhatsApp's End-to-End Encrypted Chat Backups Feature Now Rolling Out
WhatsApp end-to-end encrypted backups are now rolling out for iPhone users, Facebook has announced. Until now, WhatsApp let users back up their chat history to iCloud, but the messages and media contained in the backups weren't protected by WhatsApp's end-to-end encryption while in Apple's cloud servers. Since Apple holds the encryption keys for iCloud Backup, a subpoena of...

WhatsApp to Let Users Encrypt Chat Backups Uploaded to iCloud
WhatsApp has announced it will give its two billion users the option to upload their chat backups to Apple's iCloud using password-protected encryption. Currently, WhatsApp on iPhone lets users back up their chat history to iCloud, but messages and media that users back up aren't protected by WhatsApp's end-to-end encryption while in Apple's cloud servers. Given that Apple...
Zoom to Pay $85 Million to Users for Misleading Encryption Claims
As part of a class action lawsuit settlement, Zoom says it will pay $85 million to users for misleading them about offering end-to-end encryption on its videoconferencing service. According to ArsTechnica, the company was accused of lying about its encryption description on its website and in a security white paper, as well as providing user data to Facebook and Google without users'...

WhatsApp Still Working on Password-Protected Encrypted iCloud Backups
WhatsApp is working on a way to secure users' chat backups in iCloud using password-protected encryption, according to a new report from forthcoming-feature specialist WABetaInfo. The Facebook-owned chat platform began early work on the security feature back in March 2020. Currently, WhatsApp on iPhone lets users back up their chat history to iCloud, but messages and media that users back...
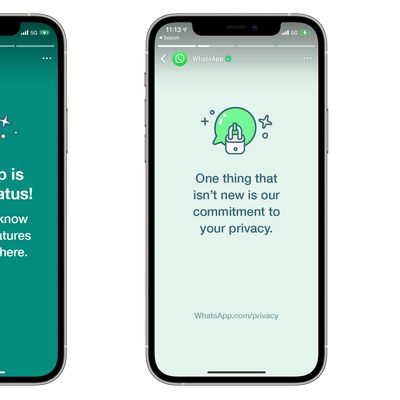
WhatsApp Uses Status Updates to Remind Users About Its Privacy Commitments
WhatsApp has started using Status messages to remind its users of the messaging service's "commitment to your privacy," following the recent confusion regarding changes to its privacy policy last month. "WhatsApp is now on Status," the message begins. "We'll let you know about new features and updates here. One thing that isn't new is our commitment to your privacy. WhatsApp can't read or...

Zoom Now Says End-to-End Encryption Will Be Available for All Users
In a U-turn by the popular videoconferencing platform, Zoom this week announced it will make end-to-end encryption available to all users, both paid and unpaid. ...we have identified a path forward that balances the legitimate right of all users to privacy and the safety of users on our platform. This will enable us to offer E2EE as an advanced add-on feature for all of our users around the...