Phishing attacks taking advantage of Apple's password reset feature have become increasingly common, according to a report from KrebsOnSecurity. Multiple Apple users have been targeted in an attack that bombards them with an endless stream of notifications or multi-factor authentication (MFA) messages in an attempt to cause panic so they'll respond favorably to social engineering.
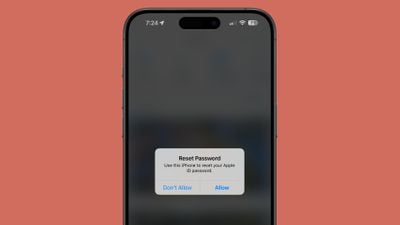
An attacker is able to cause the target's iPhone, Apple Watch, or Mac to display system-level password change approval texts over and over again. Because the password requests target the Apple ID, they pop up on all of a user's devices. The notifications render all linked Apple products unable to be used until the popups are dismissed one by one on each device. Twitter user Parth Patel recently shared his experience being targeted with the attack, and he says he could not use his devices until he clicked on "Don't Allow" for more than 100 notifications.
The actual popup can't be used to gain access to an Apple device, and it serves as a front for attackers to incite fear in the target. Following the flood of notifications, the attacker calls using a spoofed number that makes it appear to be coming from Apple. On these calls, the attacker confirms that the victim's account is under attack, and that sensitive information is needed to put a stop to it. It appears that the attacker is after a one-time code to confirm a password reset or login attempt.
In Patel's case, the attacker was using information leaked from a people search website, which included name, current address, past address, and phone number, giving the person attempting to access his account ample information to work from. The attacker happened to have his name wrong, and he also became suspicious because he was asked for a one-time code that Apple explicitly sends with a message confirming that Apple does not ask for those codes.
The attack hinges on the perpetrator having access to the email address and phone number associated with an Apple ID at a minimum, and given the description of what's been happening, it is likely that bad actors also had access to the victim's Apple ID password from database leaks and other means. One-time codes are most often triggered as secondary security, so the attacker sends the notification spam, calls the target to "save" them from the attack, logs in to the Apple ID with the stolen information and password, and triggers the one-time code. If the target hands over the code at this point, the attacker will have full access to the Apple ID.
KrebsOnSecurity looked into the issue, and found that attackers appear to be using Apple's page for a forgotten Apple ID password to send the notification spam. This page requires a user's Apple ID email or phone number, and it has a CAPTCHA. When an email address is put in, the page displays the last two digits of the phone number associated with the Apple account, and filing in the missing digits and hitting submit sends a system alert.
It is not clear how the attackers are abusing the system to send multiple messages to Apple users, but it appears to be a bug that is being exploited. It is unlikely that Apple's system is meant to be able to be used to send more than 100 requests, so presumably the rate limit is being bypassed.
Apple device owners targeted by this attack should remain calm and make sure not to provide sensitive information to someone who calls, even if the phone call appears to be coming from Apple. Spoofing a phone number is a simple thing to do, so the best course of action is to hang up and call Apple support directly. There is never a situation where a one-time code should be shared with another person, and Apple will never ask for a code.
Update: This article has been updated to clarify how the attack works. The prior version suggested that an Apple ID could be accessed should someone press "Allow" on one of the password request popups, but that is inaccurate. This is a complicated, multi-step attack that requires social engineering, but the password reset spam is a component that Apple will hopefully address in a future update.




















Top Rated Comments