Microsoft today announced that it plans to bring a version of its Defender ATP security platform to iOS and Android.
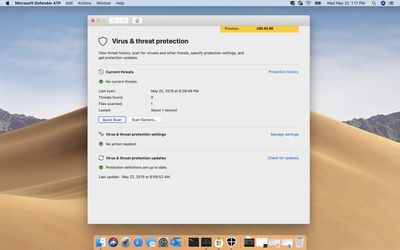
Defender ATP provides "preventive protection, post-breach detection, and automated investigation and response" for Windows and macOS, but it is unclear what the platform will offer on iOS given it is a sandboxed operating system. Existing "antivirus" apps for the iPhone typically only offer features such as identity theft and phishing prevention, website and phone call blocking, and VPN access.
Microsoft plans to share more details about Defender ATP for iOS and Android next week at the RSA Conference in San Francisco.



















Top Rated Comments
However, I don't really see the point of this on MacOS. Macs already have a malicious software detection system, and so far it's done its job pretty admirably. I suppose Defender could help find Windows malware being downloaded to a Mac before it ends up on someone's other computer or Windows VM, but that seems like a limited usage scenario.
Regardless, though, having more options is great. Bring it on!
Identity, information and device based posture in that order.