There's a vulnerability in the macOS version of the Apple Mail app that leaves some of the text of encrypted emails unencrypted, according to a report from IT specialist Bob Gendler (via The Verge).
According to Gendler, the snippets.db database file used by a macOS function that offers up contact suggestions stores encrypted emails in an unencrypted format, even when Siri is disabled on the Mac.
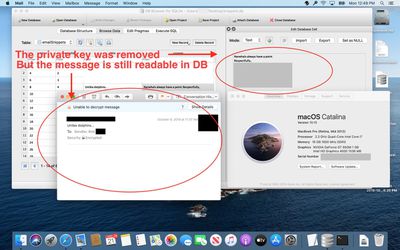
Gendler initially discovered the bug on July 29 and reported it to Apple. Over the course of several months, Apple said that it was looking into the issue, though no fix ever came. The vulnerability continues to exist in macOS Catalina and earlier versions of macOS dating back to macOS Sierra.
Let me say that again... The snippets.db database is storing encrypted Apple Mail messages...completely, totally, fully -- UNENCRYPTED -- readable, even with Siri disabled, without requiring the private key. Most would assume that disabling Siri would stop macOS from collecting information on the user. This is a big deal.
This is a big deal for governments, corporations and regular people who use encrypted email and expect the contents to be protected. Secret or top-secret information, which was sent encrypted, would be exposed via this process and database, as would trade secrets and proprietary data.
Apple told The Verge that it has been made aware of the issue and will address it in a future software update. Apple also said that only portions of some emails are stored, and provided Gendler with instructions on preventing data from being stored by the snippets database.
This issue affects a limited number of people in practice, and is not something that macOS users should generally worry about. It requires customers to be using macOS and the Apple Mail app to send encrypted emails. It does not impact those who have FileVault turned on, and a person who wanted to access the information would also need to know where in Apple's system files to look and have physical access to a machine.
Still, as Gendler points out, this particular vulnerability "brings up the question of what else is tracked and potentially improperly stored without you realizing it."
Those concerned about this issue can prevent data from being collected in the snippets.db database by opening up System Preferences, choosing the Siri section, selecting Siri Suggestions & Privacy, choosing Mail and then turning off "Learn from this App." This will stop new emails from being added to snippets.db but won't remove those that have already been included.
Apple told The Verge that customers who want to avoid unencrypted snippets being read by other apps can avoid giving apps full disk access in macOS Catalina. Turning on FileVault will also encrypt everything on the Mac.
Full details on the vulnerability can be read in Gendler's Medium article.



















