A security flaw in Apple's online store exposed the account PINs of more than 72 million T-Mobile customers, reports BuzzFeed News.
The vulnerability was discovered by security researchers Phobia and Nicholas "Convict" Ceraolo, who also found a similar flaw in the website for phone insurance company Asurion that exposed AT&T account PINs.
Both Apple and Asurion fixed the website flaws that left the PINs vulnerable after learning about them from BuzzFeed News. Apple opted not to provide further comment on the situation, but told BuzzFeed News that it is "very grateful to the researchers who found the flaw."
PINs, or passcodes, are numbers that are used as an additional account security measure by many carriers in the United States. Mobile device PINs are typically a last line of defense for a cellular account as both carrier websites and support staff will ask for the PIN for confirmation before making account changes.
SIM hacking, which uses social engineering to get carrier support staff to transfer a person's phone number to a new SIM, has become increasingly prevalent due to the number of accounts (bank, email, social media, etc.) that are tied to a person's phone number. A PIN is used as a defense mechanism against SIM hacking, which means exposed PINs can be particularly dangerous.
Accessing the T-Mobile PINs on Apple's website involved a brute force attack where a hacker used software to input multiple different numeric combinations to guess the proper one.
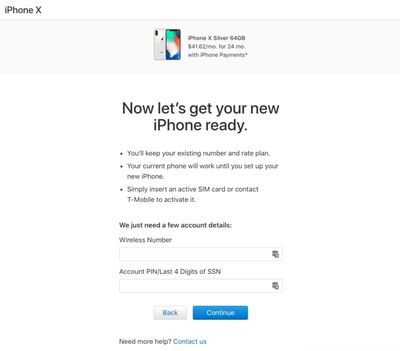
As BuzzFeed News explains, after initiating a T-Mobile iPhone purchase on the Apple online store and selecting monthly payment options through T-Mobile, Apple's site directs users to an authentication form asking for a T-Mobile number and account PIN or last four digits of a social security number (which most carriers use in place of a PIN when one has not been set).
The page allowed for infinite entry attempts into the PIN field, enabling the brute force attack that let hackers guess PINs associated with a T-Mobile phone number.
The security vulnerability appears to have been limited to T-Mobile accounts, as the same validation page for other carriers on Apple's site uses a rate limit that locks access to the form for 60 minutes after five to 10 incorrect entries. Given that the other carrier pages had rate limiting enabled, it's likely Apple made an error on the T-Mobile page.
According to Ceraolo, the vulnerability is likely due to an engineering mistake made when connecting T-Mobile's account validation API to Apple's website.
A similar vulnerability on Asurion's website exposed an unspecified number of AT&T account PINs. An AT&T spokesperson said that it is working with Asurion to investigate the issue and will "take any additional action that may be appropriate."
A phone number was required for both of these attacks, limiting the number of people who may have been impacted, but AT&T and T-Mobile customers who are concerned about their account safety should choose a new PIN.