iOS Vulnerability Prevents VPNs From Encrypting All Traffic
A vulnerability affecting iOS 13.3.1 and later prevents virtual private networks (VPNs) from encrypting all traffic, allowing some internet connections to bypass encryption, potentially exposing users' data and IP addresses.
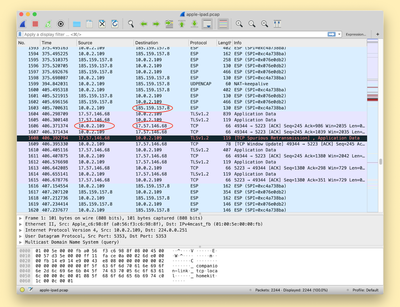
A screenshot from ProtonVPN demonstrating exposed connections to Apple's servers that should be protected by the VPN
Details on the vulnerability were shared today by Bleeping Computer after it was discovered by ProtonVPN. The vulnerability is caused because iOS isn't terminating all existing connections when a user connects to a VPN, allowing them to reconnect to destination servers once the VPN tunnel has been established.
Connections made after connecting to a VPN on an iOS are not affected by this bug, but all previously established connections are not secure. This could potentially lead to a user who believes they are protected accidentally exposing IP an address and therefore, an approximate location.
Apple's Push Notifications are cited as an example of a process using connections on Apple's servers that aren't closed automatically when connecting to a VPN, but it can affect any app or service running on a user's device.
VPNs cannot work around the issue because iOS does not allow VPN apps to kill existing network connections, so this is a fix that will need to be implemented by Apple. Apple is aware of the vulnerability and is looking into options to mitigate it.
Until fixed, VPN users can connect to a VPN server, turn on Airplane Mode and then turn off Airplane Mode to kill all existing connections. The mitigation isn't entirely reliable, however, so iPhone and iPad owners who rely on VPNs should be careful until Apple puts out a fix.
Popular Stories
Apple's next-generation iPhone 17 Pro and iPhone 17 Pro Max are less than three months away, and there are plenty of rumors about the devices.
Apple is expected to launch the iPhone 17, iPhone 17 Air, iPhone 17 Pro, and iPhone 17 Pro Max in September this year.
Below, we recap key changes rumored for the iPhone 17 Pro models:Aluminum frame: iPhone 17 Pro models are rumored to have an...
The long wait for an Apple Watch Ultra 3 appears to be nearly over, and it is rumored to feature both satellite connectivity and 5G support.
Apple Watch Ultra's existing Night Mode
In his latest Power On newsletter, Bloomberg's Mark Gurman said that the Apple Watch Ultra 3 is on track to launch this year with "significant" new features, including satellite connectivity, which would let you...
The upcoming iPhone 17 Pro and iPhone 17 Pro Max are rumored to have a slightly different MagSafe magnet layout compared to existing iPhone models, and a leaked photo has offered a closer look at the supposed new design.
The leaker Majin Bu today shared a photo of alleged MagSafe magnet arrays for third-party iPhone 17 Pro cases. On existing iPhone models with MagSafe, the magnets form a...
iOS 26 and iPadOS 26 add a smaller yet useful Wi-Fi feature to iPhones and iPads.
As spotted by Creative Strategies analyst Max Weinbach, sign-in details for captive Wi-Fi networks are now synced across iPhones and iPads running iOS 26 and iPadOS 26. For example, while Weinbach was staying at a Hilton hotel, his iPhone prompted him to fill in Wi-Fi details from his iPad that was already...
The iPhone 17 Pro Max will feature the biggest ever battery in an iPhone, according to the Weibo leaker known as "Instant Digital."
In a new post, the leaker listed the battery capacities of the iPhone 11 Pro Max through to the iPhone 16 Pro Max, and added that the iPhone 17 Pro Max will feature a battery capacity of 5,000mAh:
iPhone 11 Pro Max: 3,969mAh
iPhone 12 Pro Max: 3,687mAh...
Apple today seeded the second betas of upcoming iOS 18.6 and iPadOS 18.6 updates to public beta testers, with the betas coming just a day after Apple provided the betas to developers. Apple has also released a second beta of macOS Sequoia 15.6.
Testers who have signed up for beta updates through Apple's beta site can download iOS 18.6 and iPadOS 18.6 from the Settings app on a compatible...
Apple is developing a MacBook with the A18 Pro chip, according to findings in backend code uncovered by MacRumors.
Subscribe to the MacRumors YouTube channel for more videos.
Earlier today, Apple analyst Ming-Chi Kuo reported that Apple is planning to launch a low-cost MacBook powered by an iPhone chip. The machine is expected to feature a 13-inch display, the A18 Pro chip, and color options...




















