Apple Responds to 'Masque Attack' Vulnerability, Not Aware of Customers Affected by Attack
Just a couple days after the discovery of an iOS vulnerability referred to as Masque Attack because of its ability to emulate and replace existing legitimate apps with malicious ones, Apple has responded in a statement to iMore.
"We designed OS X and iOS with built-in security safeguards to help protect customers and warn them before installing potentially malicious software," an Apple spokesperson told iMore. "We're not aware of any customers that have actually been affected by this attack. We encourage customers to only download from trusted sources like the App Store and to pay attention to any warnings as they download apps. Enterprise users installing custom apps should install apps from their company's secure website."
Masque Attack works by luring a user to install an app outside of the iOS App Store by clicking a phishing link in a text message or email. For example, a user could be prompted to download a new app in a text message that says something like "Hey, try out Flappy Bird 2". A user is then directed to a website where they're prompted to download the app, which will install the fake app over the legitimate one using iOS enterprise provision profiles, making it virtually undetectable.
Masque Attack in action
Earlier today, the United States government
issued a warning about Masque Attack to iOS users. The vulnerability was discovered just a week after reports of malware called
WireLurker surfaced. WireLurker is able to attack iOS devices through OS X using a USB cable. Both vulnerabilities are unlikely to affect the average iOS user as long as Apple's security features are not bypassed.
Both WireLurker and Masque Attack can be avoided by staying away from suspicious apps and avoiding links that prompt users to install apps outside of Apple's App Stores.
Popular Stories
Apple's next-generation iPhone 17 Pro and iPhone 17 Pro Max are less than three months away, and there are plenty of rumors about the devices.
Apple is expected to launch the iPhone 17, iPhone 17 Air, iPhone 17 Pro, and iPhone 17 Pro Max in September this year.
Below, we recap key changes rumored for the iPhone 17 Pro models:Aluminum frame: iPhone 17 Pro models are rumored to have an...
Apple is developing a MacBook with the A18 Pro chip, according to findings in backend code uncovered by MacRumors.
Earlier today, Apple analyst Ming-Chi Kuo reported that Apple is planning to launch a low-cost MacBook powered by an iPhone chip. The machine is expected to feature a 13-inch display, the A18 Pro chip, and color options that include silver, blue, pink, and yellow.
MacRumors...
In 2020, Apple added a digital car key feature to its Wallet app, allowing users to lock, unlock, and start a compatible vehicle with an iPhone or Apple Watch. The feature is currently offered by select automakers, including Audi, BMW, Hyundai, Kia, Genesis, Mercedes-Benz, Volvo, and a handful of others, and it is set to expand further.
During its WWDC 2025 keynote, Apple said that 13...
Apple hasn't updated the AirPods Pro since 2022, and the earbuds are due for a refresh. We're counting on a new model this year, and we've seen several hints of new AirPods tucked away in Apple's code. Rumors suggest that Apple has some exciting new features planned that will make it worthwhile to upgrade to the latest model.
Subscribe to the MacRumors YouTube channel for more videos.
Heal...
Apple is planning to launch a low-cost MacBook powered by an iPhone chip, according to Apple analyst Ming-Chi Kuo.
In an article published on X, Kuo explained that the device will feature a 13-inch display and the A18 Pro chip, making it the first Mac powered by an iPhone chip. The A18 Pro chip debuted in the iPhone 16 Pro last year. To date, all Apple silicon Macs have contained M-series...
Popular accessory maker Anker this month launched two separate recalls for its power banks, some of which may be a fire risk.
The first recall affects Anker PowerCore 10000 Power Banks sold between June 1, 2016 and December 31, 2022 in the United States. Anker says that these power banks have a "potential issue" with the battery inside, which can lead to overheating, melting of plastic...
Chase this week announced a series of new perks for its premium Sapphire Reserve credit card, and one of them is for a pair of Apple services.
Specifically, the credit card now offers complimentary annual subscriptions to Apple TV+ and Apple Music, a value of up to $250 per year.
If you are already paying for Apple TV+ and/or Apple Music directly through Apple, those subscriptions will...
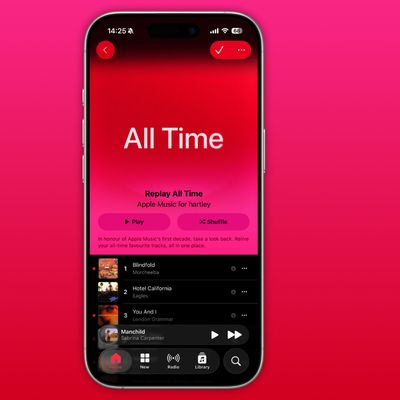
As part of its 10-year celebrations of Apple Music, Apple today released an all-new personalized playlist that collates your entire listening history.
The playlist, called "Replay All Time," expands on Apple Music's existing Replay features. Previously, users could only see their top songs for each individual calendar year that they've been subscribed to Apple Music, but now, Replay All...