macOS Big Sur 11.4 Addresses Vulnerability That Could Let Attackers Take Secret Screenshots
macOS Big Sur 11.4, which was released this morning, addresses a zero-day vulnerability that could allow attackers to piggyback off of apps like Zoom, taking secret screenshots and surrepetiously recording the screen.
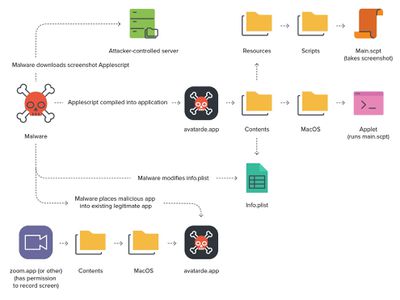
Jamf, a mobile device management company, today highlighted a security issue that allowed Privacy preferences to be bypassed, providing an attacker with Full Disk Access, Screen Recording, and other permissions without a user's consent.
The bypass was actively exploited in the wild, and was discovered by Jamf when analyzing XCSSET malware. The XCSSET malware has been out in the wild since 2020, but Jamf noticed an uptick in recent activity and discovered a new variant.
Once installed on a victim's system, the malware was used specifically for taking screenshots of the user's desktop with no additional permissions required. Jamf said that it could be used to bypass other permissions as well, as long as the donor application the malware piggybacked off of had that permission enabled.
Jamf has a full rundown on how the exploit worked, and the company says that Apple addressed the vulnerability in macOS Big Sur 11.4, Apple confirmed to TechCrunch that a fix has indeed been enabled in macOS 11.4, so Mac users should update their software as soon as possible.
Popular Stories
A new Apple TV is expected to be released later this year, and a handful of new features and changes have been rumored for the device.
Below, we recap what to expect from the next Apple TV, according to rumors.
Rumors
Faster Wi-Fi Support
The next Apple TV will be equipped with Apple's own combined Wi-Fi and Bluetooth chip, according to Bloomberg's Mark Gurman. He said the chip supports ...
Apple will launch its new iPhone 17 series in two months, and the iPhone 17 Pro models are expected to get a new design for the rear casing and the camera area. But more significant changes to the lineup are not expected until next year, when the iPhone 18 models arrive.
If you're thinking of trading in your iPhone for this year's latest, consider the following features rumored to be coming...
Apple's next-generation iPhone 17 Pro and iPhone 17 Pro Max are only two months away, and there are plenty of rumors about the devices.
Below, we recap key changes rumored for the iPhone 17 Pro models.
Latest Rumors
These rumors surfaced in June and July:A redesigned Dynamic Island: It has been rumored that all iPhone 17 models will have a redesigned Dynamic Island interface — it might ...
The long wait for an Apple Watch Ultra 3 is nearly over, and a handful of new features and changes have been rumored for the device.
Below, we recap what to expect from the Apple Watch Ultra 3:Satellite connectivity for sending and receiving text messages when Wi-Fi and cellular coverage is unavailable
5G support, up from LTE on the Apple Watch Ultra 2
Likely a wide-angle OLED display that ...
iPhone 17 Pro and iPhone 17 Pro Max models with displays made by BOE will be sold exclusively in China, according to a new report.
Last week, it emerged that Chinese display manufacturer BOE was aggressively ramping up its OLED production capacity for future iPhone models as part of a plan to recapture a major role in Apple's supply chain.
Now, tech news aggregator Jukan Choi reports...
The iOS 26 public beta release is quickly approaching, while developers have recently gotten their hands on a third round of betas that has seen Apple continue to tweak features, design, and functionality.
We're also continuing to hear rumors about the iPhone 17 lineup that is now just about right around the corner, while Apple's latest big-budget film appears to be taking off, so read on...




















