A sudo bug that can grant an attacker root access has been discovered to affect macOS Big Sur (via ZDNet).
The security vulnerability, identified last week as "CVE-2021-3156" by the Qualys Security Team, affects sudo, which is a program that allows users to run commands with the security privileges of another user, such as an administrator. The bug triggers a "heap overflow" in sudo that changes the current user's privileges to enable root-level access. This can give an attacker access to the entire system. An attacker would need to gain low-level access to a system first to be able to exploit the bug, such as via planted malware.
Sudo is part of many Unix-like systems, including macOS, but it was initially unknown if the vulnerability affected Mac machines since it was only tested by Qualys on Ubuntu, Debian, and Fedora. Security researcher Matthew Hickey has now confirmed that the most recent version of macOS, macOS Big Sur 11.2 can be subject to the sudo attack.
CVE-2021-3156 also impacts @apple MacOS Big Sur (unpatched at present), you can enable exploitation of the issue by symlinking sudo to sudoedit and then triggering the heap overflow to escalate one's privileges to 1337 uid=0. Fun for @p0sixninja pic.twitter.com/tyXFB3odxE — Hacker Fantastic 📡 (@hackerfantastic) February 2, 2021
Last week, there was speculation that the macOS Big Sur 11.2 update may address the sudo vulnerability, though it was not definitively known at the time if the bug would affect macOS. While it was found that sudo was left unchanged in macOS Big Sur 11.2, it is now clear that macOS is affected by the exploit.
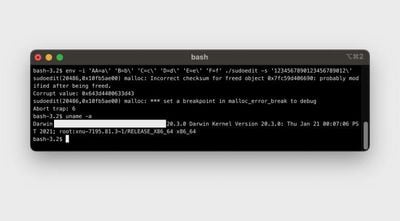
With some minor modifications, Hickey found that the sudo bug could be used to grant attackers access to macOS root accounts, and the discovery has now been verified by Carnegie Mellon University vulnerability analyst Will Dormann.
Can confirm with macOS Big Sur on both x86_64 and aarch64. pic.twitter.com/nQqQ8rskv7 — Will Dormann (@wdormann) February 2, 2021
Apple has reportedly been notified of the CVE-2021-3156 vulnerability, and due to the severity of the issue, a patch will likely be released soon.

















