Transmission Malware Transmitted Through Server Hack, Downloaded 6,500 Times
Over the weekend, the first instance of Mac ransomware was found in a malicious update to the Transmission BitTorrent client. Version 2.90 of Transmission downloaded from the Transmission website was infected with "KeRanger" ransomware.
"Ransomware" is a class of malware that encrypts a user's hard drive and files, demanding money to decrypt it. In this case, KeRanger would have required Mac users to shell out a bitcoin for decryption, equivalent to approximately $400.
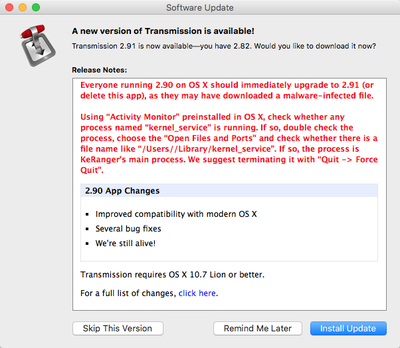
The developers behind Transmission have shared some additional details on the attack with Reuters, giving us some insight into how it occurred. The server that delivers the Transmission software to customers was breached in a cyber attack, allowing the KeRanger malware to be added to the disk-image of its software.
Transmission representative John Clay told Reuters via email that the ransomware was added to disk-image of its software after the project's server was compromised in a cyber attack.
"We're not commenting on the avenue of attack, other than to say that it was our main server that was compromised," he said. "The normal disk image (was) replaced by the compromised one."
During the time that the malware-infected version of Transmission was available, it was downloaded approximately 6,500 times before the vulnerability was discovered. Security on the server has since been increased, ensuring a similar attack can't occur a second time.
On Sunday, Transmission's developers released software updates to block the malicious software and to remove it from the Macs of users who had unwittingly installed the malicious version. Apple also updated its software protections to keep the malware from affecting Mac users and to prevent the bad version from being installed on additional machines.
Customers who have downloaded the Transmission BitTorrent client should make sure they have updated the software to version 2.92, which will remove the malware from infected computers. Additional details on how to determine if you have the malware installed are available through Palo Alto Networks.
Popular Stories
A new Apple TV is expected to be released later this year, and a handful of new features and changes have been rumored for the device.
Below, we recap what to expect from the next Apple TV, according to rumors.
Rumors
Faster Wi-Fi Support
The next Apple TV will be equipped with Apple's own combined Wi-Fi and Bluetooth chip, according to Bloomberg's Mark Gurman. He said the chip supports ...
Apple will launch its new iPhone 17 series in two months, and the iPhone 17 Pro models are expected to get a new design for the rear casing and the camera area. But more significant changes to the lineup are not expected until next year, when the iPhone 18 models arrive.
If you're thinking of trading in your iPhone for this year's latest, consider the following features rumored to be coming...
Apple's next-generation iPhone 17 Pro and iPhone 17 Pro Max are only two months away, and there are plenty of rumors about the devices.
Below, we recap key changes rumored for the iPhone 17 Pro models.
Latest Rumors
These rumors surfaced in June and July:A redesigned Dynamic Island: It has been rumored that all iPhone 17 models will have a redesigned Dynamic Island interface — it might ...
The long wait for an Apple Watch Ultra 3 is nearly over, and a handful of new features and changes have been rumored for the device.
Below, we recap what to expect from the Apple Watch Ultra 3:Satellite connectivity for sending and receiving text messages when Wi-Fi and cellular coverage is unavailable
5G support, up from LTE on the Apple Watch Ultra 2
Likely a wide-angle OLED display that ...
iPhone 17 Pro and iPhone 17 Pro Max models with displays made by BOE will be sold exclusively in China, according to a new report.
Last week, it emerged that Chinese display manufacturer BOE was aggressively ramping up its OLED production capacity for future iPhone models as part of a plan to recapture a major role in Apple's supply chain.
Now, tech news aggregator Jukan Choi reports...
The iOS 26 public beta release is quickly approaching, while developers have recently gotten their hands on a third round of betas that has seen Apple continue to tweak features, design, and functionality.
We're also continuing to hear rumors about the iPhone 17 lineup that is now just about right around the corner, while Apple's latest big-budget film appears to be taking off, so read on...



















