Early this morning, independent security researcher Ibrahim Balic speculated that he may be responsible for the security breach that caused an extended outage of Apple's Developer Center, which has been offline since late last week.
Despite Balic's claim that he reported his findings directly to Apple and did not intend to act maliciously, information that he gave in an interview with TechCrunch suggests somewhat questionable behavior.
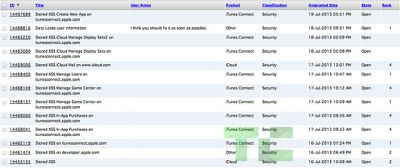
Balic, who has reported 13 different bugs to Apple, originally discovered an iAd Workbench vulnerability on June 18 that allowed a request sent to the server to be manipulated. This security hole could be used to acquire the names and email addresses of iTunes users (even non-developers). After finding the loophole, Balic wrote a Python script to harvest data from the vulnerability and then displayed it in a YouTube video, which may have put him on Apple's radar.
In addition to the iAd Workbench bug, Balic also discovered and submitted a report on a bug that caused the Dev Center site to be vulnerable to a stored XSS attack. While Balic says that it was possible to access user data by exploiting the Dev Center issue, he claims that he did not do so. According to TechCrunch, Balic's YouTube video (which has since been removed) contained full names and email addresses, and it is unclear where they originated.
It's too bad, though, that the video seemed so definitive: After showing off images of Apple's downed Dev Center and the company's official response, Balic then showed a slew of files that seem to contain full names and email addresses. It seems pretty damning, but Balic says that he never went after the Developer Center site directly, and all that user information he highlighted came from the iAd Workbench. Two separate bugs paved the way for one very confusing video.
Balic claims that he harvested data on 73 Apple employees and 100,000 other iTunes users, but he says that he did not use the Developer Center exploit that he first submitted on July 16, instead garnering the data from the iAd Workbench issue.
TechCrunch reports that the data that Balic gained (limited to email addresses and Apple IDs) may have come from non-developer accounts, though Apple has clearly stated that only developer accounts were affected.
Throughout our conversation, Balic maintained that he was only ever trying to help Apple. When asked why he downloaded all that user data rather than simply reporting the bug, Balic says he just wanted to see how "deep" he could go. If he wanted to do ill, he says, he wouldn't have reported everything he found. For what it's worth, he also says he never attempted to reset anyone's password — the farthest he went was to email one of the addresses he had discovered and ask if it was really the person's Apple ID. Balic didn't get a response.
Due to the ambiguity of the source of the names and email addresses shown in Balic's video, it is unclear whether or not he caused the Dev Center outage by manipulating the iAd Workbench bug and it is equally unclear what his intentions were.