Apple Releases Flashback Removal Tool for Macs Running OS X Lion without Java
Following yesterday's release of fresh Java updates to remove the Flashback malware system from Macs running OS X Lion and Snow Leopard, Apple today released a standalone Flashback malware removal tool to clean infections from OS X Lion systems without Java installed.
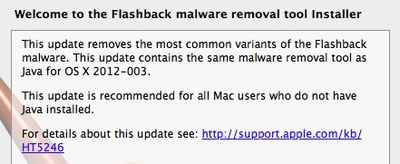
About Flashback malware removal tool
This Flashback malware removal tool that will remove the most common variants of the Flashback malware.
If the Flashback malware is found, a dialog will be presented notifying the user that malware was removed.
In some cases, the Flashback malware removal tool may need to restart your computer in order to completely remove the Flashback malware.
This update is recommended for all OS X Lion users without Java installed.
While the most dangerous method of attack for Flashback exploits a security hole in Java that Apple has now patched, various versions of the malware have also used social engineering and other tricks in attempting to gain access to users' systems.
With OS X Lion not having Java included by default, users of Apple's latest operating system who have found themselves infected through other means and do not have Java installed can use the new tool to clean their systems without needing to install Java.
The update weighs in at 356 KB and requires OS X Lion without Java installed.
Popular Stories
Apple will launch its new iPhone 17 series in two months, and the iPhone 17 Pro models are expected to get a new design for the rear casing and the camera area. But more significant changes to the lineup are not expected until next year, when the iPhone 18 models arrive.
If you're thinking of trading in your iPhone for this year's latest, consider the following features rumored to be coming...
In select U.S. states, residents can add their driver's license or state ID to the Wallet app on the iPhone and Apple Watch, providing a convenient and contactless way to display proof of identity or age at select airports and businesses, and in select apps.
Unfortunately, this feature continues to roll out very slowly since it was announced in 2021, with only nine U.S. states, Puerto Rico,...
Apple does not plan to refresh any Macs with updated M5 chips in 2025, according to Bloomberg's Mark Gurman. Updated MacBook Air and MacBook Pro models are now planned for the first half of 2026.
Gurman previously said that Apple would debut the M5 MacBook Pro models in late 2025, but his newest report suggests that Apple is "considering" pushing them back to 2026. Apple is now said to be...
Three out of four iPhone 17 models will feature more RAM than the equivalent iPhone 16 models, according to a new leak that aligns with previous rumors.
The all-new iPhone 17 Air, the iPhone 17 Pro, and the iPhone 17 Pro Max will each be equipped with 12GB of RAM, according to Fixed Focus Digital, an account with more than two million followers on Chinese social media platform Weibo. The...
Since the iPhone X in 2017, all of Apple's highest-end iPhone models have featured either stainless steel or titanium frames, but it has now been rumored that this design decision will be coming to an end with the iPhone 17 Pro models later this year.
In a post on Chinese social media platform Weibo today, the account Instant Digital said that the iPhone 17 Pro models will have an aluminum...
Production of foldable OLED displays for Apple's first foldable iPhone have begun ahead of its expected launch next year, Korea's ETNews reports.
The first foldable iPhone's displays are being produced by Samsung Display, who are establishing a production line dedicated to the upcoming Apple device its A3 factory in Asan, Chungcheongnam-do. The production line will make displays exclusively...
A new Apple TV is expected to be released later this year, and a handful of new features and changes have been rumored for the device.
Below, we recap what to expect from the next Apple TV, according to rumors.
Rumors
Faster Wi-Fi Support
The next Apple TV will be equipped with Apple's own combined Wi-Fi and Bluetooth chip, according to Bloomberg's Mark Gurman. He said the chip supports ...
iPhone 17 Pro and iPhone 17 Pro Max models with displays made by BOE will be sold exclusively in China, according to a new report.
Last week, it emerged that Chinese display manufacturer BOE was aggressively ramping up its OLED production capacity for future iPhone models as part of a plan to recapture a major role in Apple's supply chain.
Now, tech news aggregator Jukan Choi reports...



















