NPR Yesterday wrote a story on the efforts of tech companies to protect consumer data, which included an extensive chart on how companies measure up when it comes to encryption.
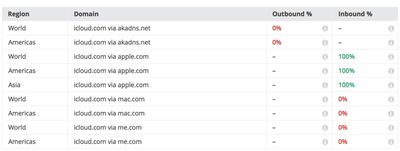
While Apple was found to be encrypting iMessage end-to-end, as well as email from customers to iCloud, it was found to be one of the few global email providers based in the U.S. that does not encrypt customer email in transit between providers. That means emails that are sent from iCloud to iCloud are encrypted, but emails sent from iCloud to other providers, such as Gmail, are not encrypted.
Following the post, however, Apple told NPR that it is planning to encrypt those emails in the near future.
Apple encrypts e-mail from its customers to iCloud. However, Apple is one of the few global email providers based in the U.S. that is not encrypting any of its customers' email in transit between providers. After we published, the company told us this would soon change. This affects users of me.com and mac.com email addresses.
As noted by 9to5Mac, Apple's response to NPR mentions only Me.com and Mac.com without a mention of the newer iCloud.com email addresses, but Google's data protection transparency website suggests that outbound iCloud.com emails are not encrypted, so it is likely Apple's plans include changes to the iCloud.com domain as well.
As noted by NPR, end-to-end encryption of emails sent back and forth between service providers requires cooperation between providers. Both email services involved (such as Apple and Google or Apple and Yahoo) must implement encryption, which means Apple will need to work with other email providers for true end-to-end encryption of iCloud.com email.
NPR's study also noted that many app installations and iOS updates are sent unencrypted to iPhones, as are configuration files sent from telecom companies, and pre-login browsing/shopping traffic from the Apple Store.























Top Rated Comments
Ok, maybe God. But that's about it. Maybe Q.
Method #1 - Encrypt the pipe that the email message travels through. This is basically the whole SSL/TLS discussion that has been in the news lately.
Method #2 - Encrypt the contents of the email message itself. This would allow the encrypted message to pass through non-encrypted pipes and still be safe. But this method is far more complicated, as it requires a certificate+handshake between the sending email client and the receiving email client.
It sounds like Apple will be ensuring that when it connects to another mail server, it will try to use an encrypted pipe, if the other server supports that whereas right now, it doesn't make that effort. That would make sense. The messages themselves won't be magically encrypted as per Method #2. That's up to the end-user to implement.
If Apple is encrypting them with Apple's keys, this has no effect on the government because Apple can simply be ordered to hand them over, just like Lavabit was.
Apple really needs to have customers generate their own keys locally and only pass encrypted data through Apple servers to address the NSL issue. If Apple doesn't hold the keys, they can't surrender them if served with an NSL.
Then Snowden/Greenwald released a talk slide from the NSA showing that tapping those messages between server farms was one of the ways they were intercepting (specifically) Google data. That slide was shown to a pair of Google engineers, who then reportedly responded "oh (expletive)".
Google does deserve credit for moving on this quickly - but all of these companies have been playing catch-up. And really this only addresses spying by national entities. This almost certainly isn't how criminals get hold of people's mail.