Pwn2Own
By MacRumors Staff
Pwn2Own Articles

Pwn2Own Hacking Competition Returns in March, Up to $130,000 in Prizes Available for Safari Vulnerabilities
Trend Micro today announced that its annual Pwn2Own hacking competition will be held March 18-20 in Vancouver, Canada.
Pwn2Own, part of the CanSecWest conference, tasks security researchers with uncovering vulnerabilities in operating systems, web browsers, and more, ranging from macOS and Windows to Safari and Chrome.
This year, two prizes will be available for Safari on macOS, including ...
Read Full Article 7 comments

Two Zero-Day Vulnerabilities Discovered in Safari for Mac on Day One of Pwn2Own Hacking Contest
The 19th annual CanSecWest security conference is underway in Vancouver, Canada, including the annual Pwn2Own hacking contest, and two zero-day security vulnerabilities have so far been discovered in Safari on macOS.
The contest kicked off on Wednesday with security researchers Amat Cama and Richard Zhu teaming up against Safari. The duo successfully exploited the browser and escaped the...

Researchers Uncover macOS and Safari Exploits at Pwn2Own 2018 [Updated]
The eighteenth annual CanSecWest security conference is underway in downtown Vancouver, Canada, where researchers are competing in the 11th Pwn2Own computer hacking contest for over $2 million in prizes.
Day one results have already been published over at the Zero Day Initiative website, with a couple of successful Mac-related exploits already appearing in the list of achievements.
Image ...

Security Researchers Use Wi-Fi and Safari Exploits to Breach iPhone 7 at Annual Mobile Pwn2Own Contest
Trend Micro's annual Mobile Pwn2Own contest took place in Tokyo, Japan today at the PacSec security conference, and security researchers spent the day attempting to hack into the iPhone 7, the Samsung Galaxy S8, the Google Pixel, and the Huawei Mate 9 Pro in an effort to win prizes totaling more than $500,000.
Apple's iPhone 7, running iOS 11.1, the latest version of the iOS 11 operating...

Mobile Pwn2Own Contest Offering Up to $100,000 Reward for iOS Vulnerabilities
Japanese cybersecurity company Trend Micro today announced its sixth annual Mobile Pwn2Own competition will be held at this year's PacSec security conference in Tokyo on Wednesday, November 1 and Thursday, November 2.
The competition is part of Trend Micro's Zero Day Initiative, a program for rewarding security researchers for responsibly disclosing vulnerabilities to companies like Apple,...
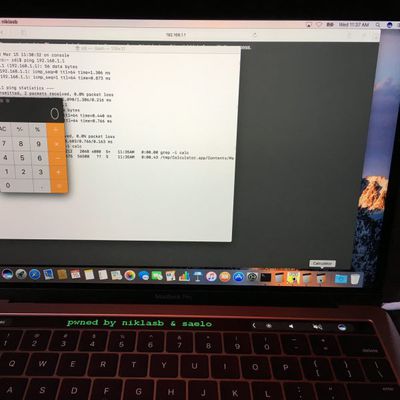
Researchers Uncover macOS and Safari Exploits at Pwn2Own 2017
The seventeenth annual CanSecWest security conference is underway in downtown Vancouver, British Columbia, where researchers are competing in the 10th anniversary Pwn2Own computer hacking contest for over $1 million in prizes.
Day one results have already been published over at the Zero Day Initiative website, with a couple of successful Mac-related exploits already appearing in the list of...

Researchers Uncover Multiple OS X and Safari Exploits at Pwn2Own 2016
The sixteenth annual CanSecWest security conference is underway in downtown Vancouver, British Columbia, and researchers participating in the Pwn2Own computer hacking contest have already discovered multiple vulnerabilities in OS X and the Safari web browser on the desktop.
On day one of the event, independent security researcher JungHoon Lee earned $60,000 after exploiting both OS X and...












