Exploit
By MacRumors Staff
Exploit Articles
Latest Chrome 88 Update Includes Important Fix for Zero-Day Vulnerability
Google has released Chrome version 88.0.4324.150 with an important fix for a zero-day vulnerability in the web browser that the company says is likely to have been exploited in the wild.
Google hasn't provided specific details about the heap buffer overflow memory corruption bug known as CVE-2021-21148, and says it won't do so "until a majority of users are updated with a fix."
However, ZDNe...
Read Full Article 21 comments

iOS Wi-Fi Exploit Could Have Let Hackers Remotely Access Nearby iPhones
Earlier this year, Apple patched an iOS vulnerability that potentially could have allowed hackers to remotely access a nearby iPhone and gain control of the entire device.
Devised by Ian Beer, a researcher at Project Zero, Google's vulnerability research team, the exploit used a vulnerability in Apple Wireless Direct Link (AWDL), Apple's proprietary mesh networking protocol that enables...

Apple's T2 Security Chip Vulnerable to Attack Via USB-C
After it was reported last week that Apple's T2 Security Chip could be vulnerable to jailbreaking, the team behind the exploit have released an extensive report and demonstration.
Apple's custom-silicon T2 co-processor is present in newer Macs and handles encrypted storage and secure boot capabilities, as well as several other controller features. It appears that since the chip is based on ...

Apple's T2 Chip Has Unpatchable Security Flaw, Claims Researcher [Updated]
Intel Macs that use Apple's T2 Security Chip are vulnerable to an exploit that could allow a hacker to circumvent disk encryption, firmware passwords and the whole T2 security verification chain, according to team of software jailbreakers.
Apple's custom-silicon T2 co-processor is present in newer Macs and handles encrypted storage and secure boot capabilities, as well as several other...

Apple Paid Hacker $75,000 for Uncovering Zero-Day Camera Exploits in Safari
Apple paid out $75,000 to a hacker for identifying multiple zero-day vulnerabilities in its software, some of which could be used to hijack the camera on a MacBook or an iPhone, according to Forbes.
A zero-day vulnerability refers to a security hole in software that is unknown to the software developer and the public, although it may already be known by attackers who are quietly exploiting...

Android Security Flaw Let Apps Access People's Cameras for Secret Video and Audio Recordings
A security flaw in Android smartphones from companies like Google and Samsung allowed malicious apps to record video, take photos, and capture audio, uploading the content to a remote server sans user permission.
The vulnerability was discovered by security firm Checkmarx, and was highlighted today by Ars Technica. The flaw had the potential to leave high-value targets open to having their...

Researcher Gives Apple Details of macOS Keychain Security Flaw Despite No Mac Bug Bounty Program
A German teenager who discovered a macOS Keychain security flaw last month has now shared the details with Apple, after having initially refused to hand them over because of the company's lack of a bug bounty program for the Mac.
Eighteen-year-old Linus Henze dubbed the zero-day macOS vulnerability he found "KeySteal," which, as demoed in the video above, can be used to disclose all...

Intel CEO Pledges Commitment to Security Following Meltdown and Spectre Vulnerabilities
Intel CEO Brian Krzanich today wrote an open letter to Intel customers following the "Meltdown" and "Spectre" hardware-based vulnerabilities that impact its processors.
In the letter, Krzanich says that by January 15, updates will have been issued for at least 90 percent of Intel CPUs introduced in the past five years, with updates for the remainder coming at the end of January.
For Apple...
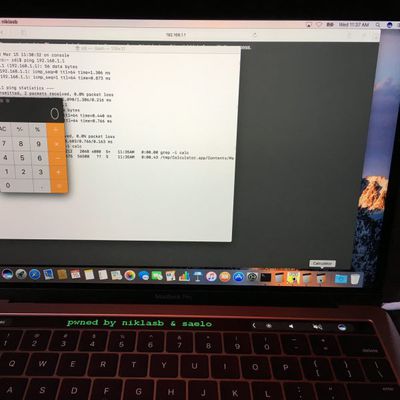
Researchers Uncover macOS and Safari Exploits at Pwn2Own 2017
The seventeenth annual CanSecWest security conference is underway in downtown Vancouver, British Columbia, where researchers are competing in the 10th anniversary Pwn2Own computer hacking contest for over $1 million in prizes.
Day one results have already been published over at the Zero Day Initiative website, with a couple of successful Mac-related exploits already appearing in the list of...
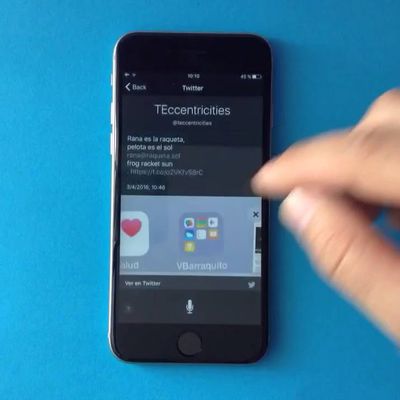
Security Flaw in iOS 9.3.1 Allows Access to iPhone Photos and Contacts
A video surfaced online yesterday purporting to show a vulnerability in iOS 9.3.1 that allows anyone to access photos and contacts on a locked iPhone without having to enter a passcode.
The YouTube video, uploaded by Jose Rodriguez and first spotted by The Daily Dot, depicts a user performing a Siri search followed by a series of relatively simple steps, one of which involves 3D Touch,...

Researchers Uncover Multiple OS X and Safari Exploits at Pwn2Own 2016
The sixteenth annual CanSecWest security conference is underway in downtown Vancouver, British Columbia, and researchers participating in the Pwn2Own computer hacking contest have already discovered multiple vulnerabilities in OS X and the Safari web browser on the desktop.
On day one of the event, independent security researcher JungHoon Lee earned $60,000 after exploiting both OS X and...
OS X 10.10.2 Includes Fix for 'Thunderstrike' Hardware Exploit Affecting Macs
Apple is readying a fix in OS X 10.10.2 for the so-called "Thunderstrike" hardware exploit targeting Macs equipped with Thunderbolt ports, iMore has learned. According to the report, Apple patched the vulnerability by making code changes in the upcoming software update that prevent a Mac's bootrom from being replaced or rolled back to a previous state in which it could be attacked.To secure...











