iOS 9.3.1
By MacRumors Staff
iOS 9.3.1 Articles

9.7-Inch iPad Pro Crashing Issues Persist for Some Users on iOS 9.3.2
Over the past six weeks, a number of 9.7-inch iPad Pro early adopters have reported sporadic crashing issues that result in the tablet soft rebooting to the Apple logo start up screen and prompting Touch ID or passcode verification.
The bug has afflicted a wide range of 9.7-inch iPad Pro models since the tablet launched on March 31, regardless of storage capacity, color, and Wi-Fi or cellular...
Read Full Article 210 comments
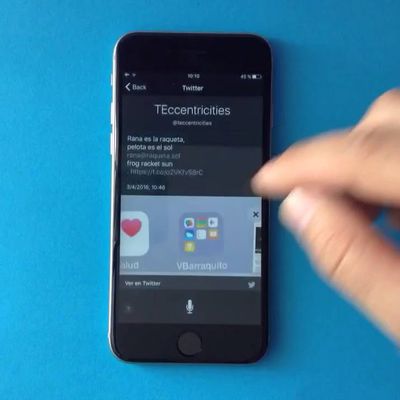
Security Flaw in iOS 9.3.1 Allows Access to iPhone Photos and Contacts
A video surfaced online yesterday purporting to show a vulnerability in iOS 9.3.1 that allows anyone to access photos and contacts on a locked iPhone without having to enter a passcode.
The YouTube video, uploaded by Jose Rodriguez and first spotted by The Daily Dot, depicts a user performing a Siri search followed by a series of relatively simple steps, one of which involves 3D Touch,...












