Cellebrite
By MacRumors Staff
Cellebrite Articles

Data Extraction Company Cellebrite Touts New Software for Cracking iPhones and iPads Running up to iOS 12.3
Israel-based software developer Cellebrite, known for breaking into mobile devices like the iPhone to obtain sensitive data, has announced that it can now unlock any iOS device running up to iOS 12.3, which was released only a month ago. The firm revealed the capability in a tweet posted late Friday advertising UFED Premium, the latest version of its Universal Forensic Extraction Device....
Read Full Article 64 comments

Cellebrite Says it Now Supports 'Lawful Unlocking' of iPhone 6 and Older Models
Cellebrite director of forensic research Shahar Tal recently tweeted out that the company's Advanced Investigative Service can now unlock and extract the full file system for the iPhone 6 and iPhone 6 Plus (via CyberScoop). To date, CAIS "supports lawful unlocking and evidence extraction" from the following iPhone generations: 4s, 5, 5c, 5s, 6, and 6 Plus. No mention has been made whether or not...

Hacker Leaks Cellebrite's iOS Bypassing Tools, Tells FBI 'Be Careful What You Wish For'
It's been nearly a year since a U.S. federal judge originally ordered Apple to help the FBI hack into an iPhone owned by Syed Farook, one of the shooters in the December 2015 attacks in San Bernardino. As we learned in the months after the initial court order -- which Apple continually opposed -- the FBI enlisted the help of Israeli mobile software developer Cellebrite to open up the iPhone 5c in ...
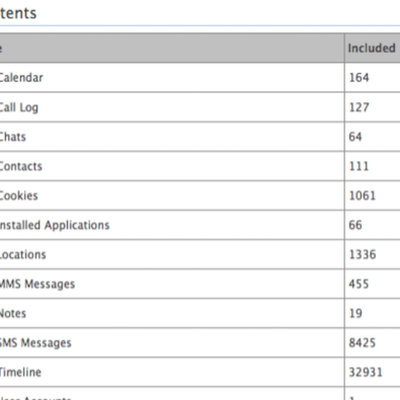
Leaked Documents Reveal What Kind of Data Cellebrite Can Extract From iPhones
Israeli mobile software developer Cellebrite gained media attention earlier this year when rumors suggested the FBI recruited the company to unlock San Bernardino shooter Syed Farook's iPhone. While the FBI did not enlist Cellebrite's help, the company does have technology licensed by governments that can extract iPhone data. ZDNet has obtained documents that reveal the scope of this technology. ...













