Security Researchers Discover XcodeSpy Malware That Targets Developers
Developers need to look out for "XcodeSpy," a malicious Xcode project that installs a custom variant of the "EggShell" backdoor on a macOS computer, according to new research shared today by SentinelOne (via Ars Technica).

Xcode is software designed for developers who want to write apps for the iOS and macOS platforms, and the malicious project that's circulating mirrors TabBarInteraction, a legitimate open source project.
Developers who download the XcodeSpy project think they're getting TabBarInteraction, but the malware includes a hidden "run Script" executable that downloads and installs the EggShell open source back door that's able to spy on users through the microphone, camera, and keyboard as well as upload and download files.
Two variants of the custom EggShell attack were found to be uploaded in Japan, first in August and then in October, so this is an attack that's been out in the wild for some time.
We have thus far been unable to discover other samples of trojanized Xcode projects and cannot gauge the extent of this activity. However, the timeline from known samples and other indicators mentioned below suggest that other XcodeSpy projects may exist. By sharing details of this campaign, we hope to raise awareness of this attack vector and highlight the fact that developers are high-value targets for attackers.
SentinelOne says that all Apple Developers that use Xcode should exercise caution when using shared Xcode projects.
Popular Stories
While the iPhone 18 Pro and iPhone 18 Pro Max are not expected to launch for another eight months, there are already plenty of rumors about the devices.
Below, we have recapped 12 features rumored for the iPhone 18 Pro models, as of January 2026:
The same overall design is expected, with 6.3-inch and 6.9-inch display sizes, and a "plateau" housing three rear cameras
Under-screen Face ID...
Apple plans to upgrade the iPad mini, MacBook Pro, iPad Air, iMac, and MacBook Air with OLED displays between 2026 and 2028, according to DigiTimes.
Bloomberg's Mark Gurman previously reported that the iPad mini and MacBook Pro will receive an OLED display as early as this year, but he does not expect the MacBook Air to adopt the technology until 2028 at the earliest.
A new iPad Air is...
Apple today updated its trade-in values for select iPhone, iPad, Mac, and Apple Watch models. Trade-ins can be completed on Apple's website, or at an Apple Store.
The charts below provide an overview of Apple's current and previous trade-in values in the United States, according to the company's website. Most of the values declined slightly, but some of the Mac values increased.
iPhone
...
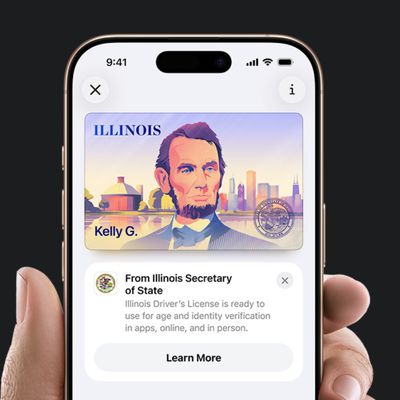
In select U.S. states, residents can add their driver's license or state ID to the Apple Wallet app on the iPhone and Apple Watch, and then use it to display proof of identity or age at select airports and businesses, and in select apps.
The feature is currently available in 13 U.S. states and Puerto Rico, and it is expected to launch in at least seven more in the future.
To set up the...
While the iPhone 18 Pro models are still around eight months away, a leaker has shared some alleged details about the devices.
In a post on Chinese social media platform Weibo this week, the account Digital Chat Station said the iPhone 18 Pro and iPhone 18 Pro Max will have the same 6.3-inch and 6.9-inch display sizes as the iPhone 17 Pro and iPhone 17 Pro Max.
Consistent with previous...