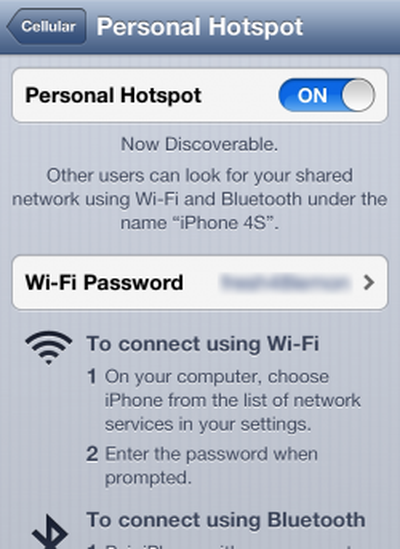
 When tethering an iPhone or an iPad, iOS users have the option of using an automatically generated password for their personal hotspots, which Apple implemented to provide all users with a secure password option.
When tethering an iPhone or an iPad, iOS users have the option of using an automatically generated password for their personal hotspots, which Apple implemented to provide all users with a secure password option.
According to researchers at Germany's University of Erlangen (via ZDNeT), the way that the keys are generated – with a combination of a short English word along with random numbers – is predictable to the point where the researchers are able to crack the hotspot password in less than a minute.
In their paper, the three researchers detail the process that they used to figure out the weak spots in the hotspot's protection. Apple's word list uses approximately 52,500 entries, so initially, cracking the hotspot took almost 50 minutes. After finding a WiFi connection, the researchers used an AMD Radeon HD 6990 GPU to run through word and number combinations.
"This list consists of around 52,500 entries, and was originated from an open-source Scrabble crossword game. Using this unofficial Scrabble word list within offline dictionary attacks, we already had a 100 percent success rate of cracking any arbitrary iOS hotspot default password," the researchers wrote.
The team discovered that only a small set of Apple's larger word list was being used, so with GPU cluster of four AMD Radeon HD 7970s, they narrowed their iOS-generated hotspot password cracking time down to just 50 seconds. In the paper, the team goes on to criticize Apple's password generation standards, suggesting that system generated passwords be composed of random letters and numbers.
"In the context of mobile hotspots, there is no need to create easily memorizable passwords. After a device has been paired once by typing out the displayed hotspot password, the entered credentials are usually cached within the associating device, and are reused within subsequent connections," the paper states.
"System-generated passwords should be reasonably long, and should use a reasonably large character set. Consequently, hotspot passwords should be composed of completely random sequences of letters, numbers, and special characters."
As noted by ZDNet though Apple's password generation system is flawed, it is a more robust solution than what is used by other companies like Microsoft. For example, the Windows 8 phone utilizes default passwords that consist of eight digit numbers.
To avoid a weak iPhone hotspot password, users can still choose to use passwords of their own creation, which should contain a sequence of random numbers and letters for enhanced security.




















Top Rated Comments
The passwords generated in the beta are not based on dictionary words and are considerably more randomized.
Using my iPad out in a park away from building WIFI. I think that, with a gas generator out in a park might be obvious and suspicious...
Also, use Bluetooth. The connection is persistent. iPad reconnects without fiddling with Phone because the phone doesn't idle it's bluetooth like it does WIFI. Also more secure as you will have to manually approve the connection. Problem solved, and everything fixed.