Changes in iOS 7 Security Make Kernel More Vulnerable to Attack
A security researcher claims changes Apple made to tighten its kernel security system in iOS 7 instead weakened the system, making it less secure than its iOS 6 counterpart. (Via CNET and ThreatPost) Azimuth Security researcher Tarjei Mandt discovered the flaw and presented his findings last week at CanSecWest.
The security flaw involves the random number generator Apple uses to secure its kernel. In iOS 6, the number generator that encrypted the kernel derived its values in part from the CPU clock counter. Because it was based on time, the encryption was only marginally secure as the output values were predictable, especially when examining successive numbers.
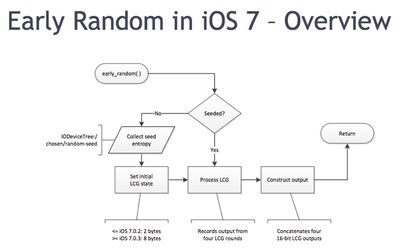
Apple was aware of the limitations in iOS 6 and attempted to tighten security in iOS 7 by changing the random number generator to a linear congruential generator, which is more susceptible to brute force attacks.
The problem with the new generator in iOS 7 is that it uses a linear recursion algorithm, Mandt said, which has "more correlation" between the values it generates. That makes them easier to extrapolate and guess, he said.
This flaw potentially allows a malicious hacker to gain kernel-level access to an iOS device via an unpatched vulnerability. The kernel is the base part of the iOS operating system and controls low-level functions such as security and resource allocation.
Apple approached Mandt about his findings and asked for his CanSecWest slide presentation.
Popular Stories
Apple has stopped production of FineWoven accessories, according to the Apple leaker and prototype collector known as "Kosutami." In a post on X (formerly Twitter), Kosutami explained that Apple has stopped production of FineWoven accessories due to its poor durability. The company may move to another non-leather material for its premium accessories in the future. Kosutami has revealed...
Apple has announced it will be holding a special event on Tuesday, May 7 at 7 a.m. Pacific Time (10 a.m. Eastern Time), with a live stream to be available on Apple.com and on YouTube as usual. The event invitation has a tagline of "Let Loose" and shows an artistic render of an Apple Pencil, suggesting that iPads will be a focus of the event. Subscribe to the MacRumors YouTube channel for more ...
The upcoming iOS 17.5 update for the iPhone includes only a few new user-facing features, but hidden code changes reveal some additional possibilities. Below, we have recapped everything new in the iOS 17.5 and iPadOS 17.5 beta so far. Web Distribution Starting with the second beta of iOS 17.5, eligible developers are able to distribute their iOS apps to iPhone users located in the EU...
Apple has dropped the number of Vision Pro units that it plans to ship in 2024, going from an expected 700 to 800k units to just 400k to 450k units, according to Apple analyst Ming-Chi Kuo. Orders have been scaled back before the Vision Pro has launched in markets outside of the United States, which Kuo says is a sign that demand in the U.S. has "fallen sharply beyond expectations." As a...
The lead developer of the multi-emulator app Provenance has told iMore that his team is working towards releasing the app on the App Store, but he did not provide a timeframe. Provenance is a frontend for many existing emulators, and it would allow iPhone and Apple TV users to emulate games released for a wide variety of classic game consoles, including the original PlayStation, SEGA Genesis,...
Apple Vision Pro, Apple's $3,500 spatial computing device, appears to be following a pattern familiar to the AR/VR headset industry – initial enthusiasm giving way to a significant dip in sustained interest and usage. Since its debut in the U.S. in February 2024, excitement for the Apple Vision Pro has noticeably cooled, according to Bloomberg's Mark Gurman. Writing in his latest Power On...




















Top Rated Comments
Couldn't have been an accident that someone missed, could it? Nah....everyone get your tin foil hats out cause everyone's out to get us.
In reality, props to white-hat hackers like Mandt
No. Apple would never do this. They never compromise on customer security for anyone.
It's very hard to say how much of a problem there actually is. My understanding - which may be wrong - is that this random number generator is used at the very early stages while iOS is booting, and is then replaced with something a lot stronger. There's the claim that the random number sequence could be predicted, but then I wonder which non-Apple software would be running on the device at the early stages when this random number generator is in use. Quite possibly none at all.