macOS High Sierra, released to the public today, could be impacted by a major security flaw that could allow a hacker to steal the usernames and passwords of accounts stored in Keychain.
As it turns out, unsigned apps on macOS High Sierra (and potentially earlier versions of macOS) can allegedly access the Keychain info and display plaintext usernames and passwords without a user's master password.
Security researcher and ex-NSA analyst Patrick Wardle tweeted about the vulnerability early this morning and shared a video of the exploit in action.
on High Sierra (unsigned) apps can programmatically dump & exfil keychain (w/ your plaintext passwords)🍎🙈😭 vid: https://t.co/36M2TcLUAn #smh pic.twitter.com/pqtpjZsSnq — patrick wardle (@patrickwardle) September 25, 2017
For this vulnerability to work, a user needs to download malicious third-party code from an unknown source, something Apple actively discourages with warnings about apps downloaded outside of the Mac App Store or from non-trusted developers. In fact, Apple does not even allow apps from non-trusted developers to be downloaded without explicitly overriding security settings.
As demonstrated in the video above, Wardle created a proof-of-concept app called "keychainStealer" that was able to access plaintext passwords stored in Keychain for Twitter, Facebook, and Bank of America. Wardle spoke to Forbes about the vulnerability and said it's actually not hard to get malicious code running on a Mac even with Apple's protections in place.
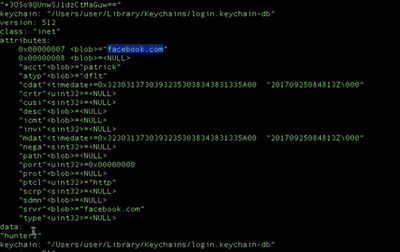
"Without root priveleges, if the user is logged in, I can dump and exfiltrate the keychain, including plaintext passwords," Wardle told Forbes. "Normally you are not supposed to be able do that programmatically."
"Most attacks we see today involve social engineering and seem to be successful targeting Mac users," he added. "I'm not going to say the [keychain] exploit is elegant - but it does the job, doesn't require root and is 100% successful."
Wardle has not provided the full exploit code for malicious entities to take advantage of, and he believes Apple will patch the problem in a future update.
As Wardle has not released the full exploit code, it has not been double-checked by MacRumors or another source, so full details on the vulnerability are not known just yet.
Apple has not yet responded to requests for comment about the potential vulnerability.

















Top Rated Comments
2. You don't know if he found this yesterday. But sure hate on the guy who might have prevented your bank account password from ending up in the wrong hands.
/irony ended